December 27, 2025
Endpoint protection software is a critical layer of cybersecurity designed to secure end-user devices such as laptops, desktops, servers, and mobile endpoints from cyber threats. As organizations adopt cloud services, remote work, and SaaS platforms, endpoints have become one of the most frequently targeted attack surfaces. This guide explains what endpoint protection software is, how it works, its core capabilities, and how to choose the right solution for your organization.
Endpoint protection software is a security solution that monitors, detects, and prevents malicious activity on endpoint devices connected to a network. Unlike traditional antivirus tools that rely mainly on known threat signatures, modern endpoint protection platforms combine behavioral analysis, machine learning, and real-time monitoring to defend against both known and unknown threats.
In practical terms, it acts as a continuous security guard on every device analyzing processes, files, network connections, and user behavior to stop attacks before they can spread or cause damage.
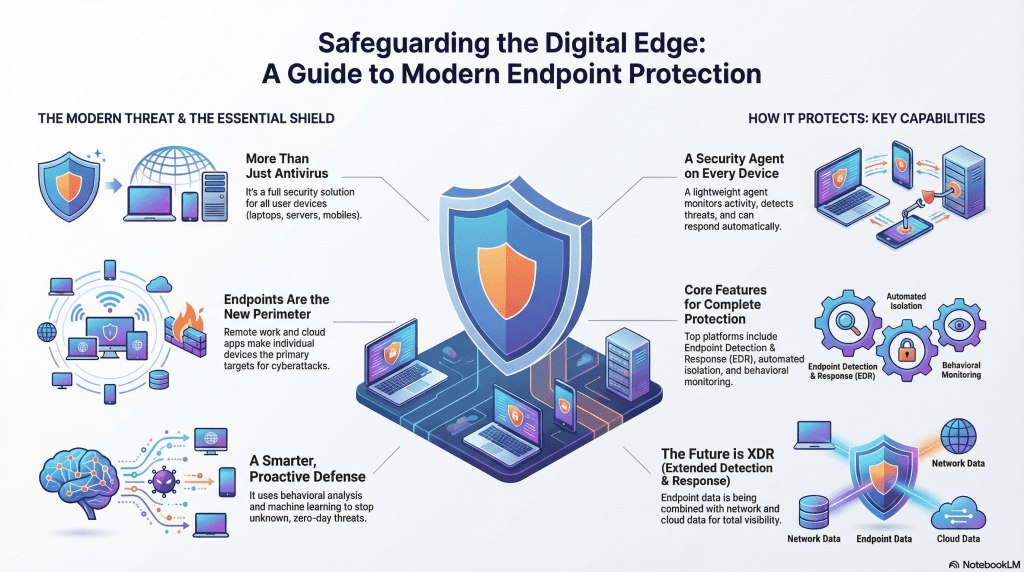
Cyberattacks have shifted from targeting centralized servers to exploiting vulnerable endpoints. Remote work, BYOD policies, and cloud-based applications mean sensitive business data now lives on hundreds or thousands of devices outside the corporate perimeter.
Endpoint protection software helps organizations:
Without strong endpoint security, even one compromised laptop can become an entry point for a full-scale breach.
Endpoint protection solutions operate through a layered security model. Each endpoint runs a lightweight agent that continuously collects telemetry such as file changes, process execution, and network activity and analyzes it locally or in the cloud.
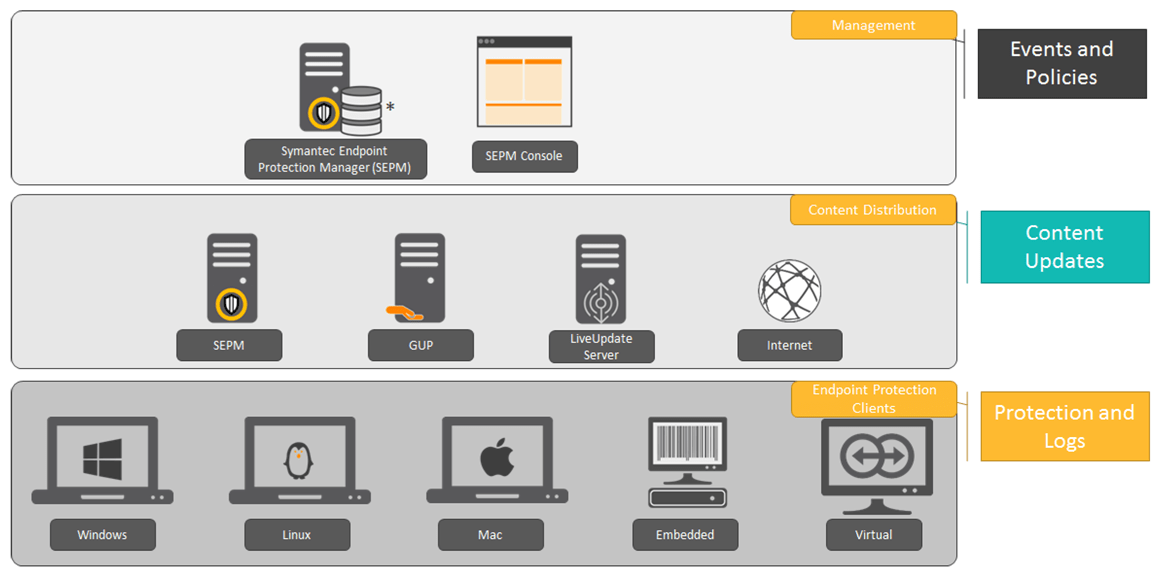
When suspicious behavior is detected, the system can automatically block the action, isolate the device, or alert security teams for investigation. Advanced platforms also retain detailed activity logs to support forensic analysis and incident response.
Modern solutions go beyond signature-based detection. They use behavioral patterns and exploit prevention techniques to stop malware, ransomware, and fileless attacks, even if the threat has never been seen before.
Machine learning models analyze normal endpoint behavior and flag anomalies such as unusual process execution or privilege escalation attempts. This allows detection of zero-day attacks that traditional antivirus tools may miss.
EDR adds continuous monitoring and historical visibility. Security teams can trace an attack timeline, identify the root cause, and respond quickly using automated or manual actions.
If a device is compromised, endpoint protection software can isolate it from the network, terminate malicious processes, or roll back system changes to prevent lateral movement.
Administrators manage all endpoints from a single dashboard, making it easier to enforce policies, monitor security posture, and generate compliance reports.
Traditional antivirus focuses primarily on detecting known threats using signature databases. While effective against older malware, it struggles with modern attack techniques.
Endpoint protection software, by contrast, uses multiple detection layers, real-time analytics, and response capabilities. This makes it far more effective in today’s threat landscape, where attacks are stealthy, fast-moving, and often custom-built.
Several platforms are widely used across enterprises and mid-sized organizations:
Each solution differs in detection depth, automation, scalability, and pricing, making selection dependent on organizational needs.
Choosing the right solution starts with understanding your environment. Organizations with remote workforces and cloud-first infrastructure often benefit from cloud-native endpoint protection with strong EDR capabilities. Smaller businesses may prioritize ease of use and cost-effectiveness, while enterprises often need advanced analytics, integrations, and automated response.
Key evaluation criteria include:
Endpoint protection is evolving toward XDR (Extended Detection and Response), where endpoint data is correlated with signals from email, identity, cloud, and network security tools. This broader visibility enables faster detection and more accurate response across the entire attack surface.
As cyber threats continue to grow in sophistication, endpoint protection software will remain a foundational element of any robust cybersecurity strategy.
Endpoint protection software is no longer optional, it is a necessity for organizations of all sizes. By combining prevention, detection, and response into a single platform, it helps businesses protect their devices, data, and users against today’s complex cyber threats. Selecting the right cyber security solution ensures not just security, but also operational resilience in an increasingly digital world.
Explore Topics

Consult with Our Techjockey Expert
Connect for fast and scalable software delivery, corporation plans, advanced security, and much more.
Compare Popular Software

Get the latest Techjockey US Blog Updates!
Subscribe to get the first notified about tech updates directly in your inbox.