PAM Explained: How Privileged Access Management Keeps Hackers Out

Hackers can’t just keep away by using strong passwords. Here’s the proof:
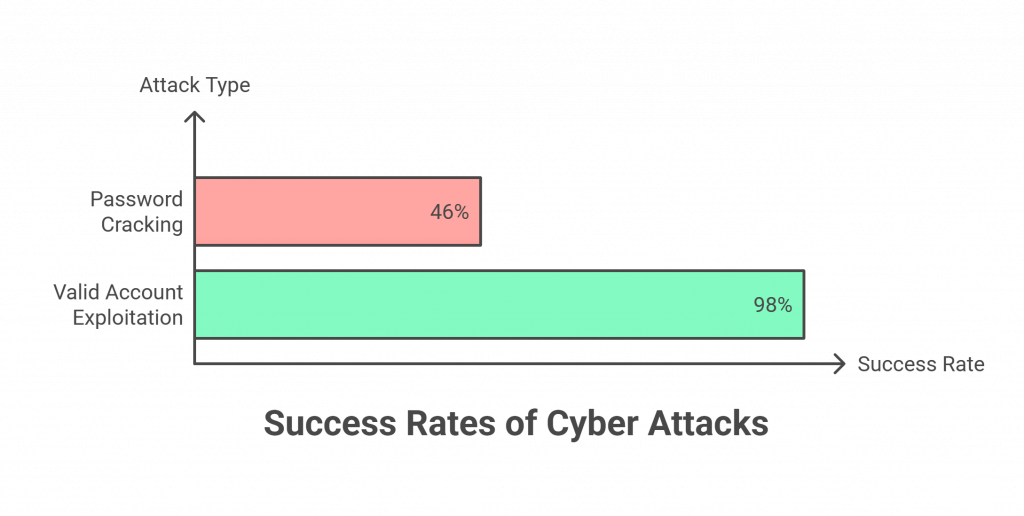
Research says that in around 46% of environments, password cracking attempts by cyber criminals are successful. However, there’s another record where valid accounts are exploited in 98% of attacks. This indicates that a cyberattack starts with stolen login details.
These numbers are only increasing with time. In 2025 alone, a massive credential breach revealed more than 16 billion login credentials, ranging from usernames to passwords, tokens, and even session cookies.
The stolen credentials can grant attackers easy access to sensitive systems. They could also make backdoors without being detected, even after several months.
It’s a reminder that no single defense is enough!
Companies now rely on a mix of cybersecurity tools and access management strategies to stay secure. One such approach is Privileged Access Management and an increasing number of companies are adopting it to protect their valuable digital assets.
This is why an increasing number of companies are adopting Privileged Access Management (PAM) to protect their valuable digital assets.
What Is Privileged Access Management?
Privileged Access Management is a strategy in cybersecurity to regulate and oversee who should have privileged access to critical systems, applications, and information. It is just like a security guard that only opens the right doors for the right people, at the right time.
PAM implements authentication, authorization, and auditing to ensure that privileged accounts are used in a responsible manner. This way, there are less chances of unauthorized access, insider threats, and accidental data leakages.
At its simplest, privileged access management follows the principle of least privilege. It provides users, systems, and processes with the minimum access necessary to get their job done.
If a marketing executive has no need for admin rights to the company server, they won’t get them.
By providing the right permissions and tracking every privileged action, PAM helps organizations shrink their attack surface and stay compliant with data protection laws.
What Are Privileged Accounts?
Privileged accounts are special user accounts that can make administrative changes or access sensitive systems. These are the master keys of your digital infrastructure.
They are used to:
- Install or update software
- Access servers and databases
- Manage IT infrastructure
- Reset passwords or modify user roles
And as privileged accounts have so much power to control the security infrastructure, they are top targets for cybercriminals.
Types of Privileged Accounts
There are several types of privileged accounts:
- Local administrative accounts: In this, the access is limited to a specific computer or server.
- Domain admin accounts: Control across all devices and users within a network domain
- Service accounts: Used by applications to interact with systems
- Application accounts: Allow apps to connect to databases or other tools
- Emergency (break-glass) accounts: Used temporarily during crises
- Non-human or machine accounts: Created for bots, scripts, or AI tools that need system access
As automation and AI grow, machine identities now outnumber human ones, making PAM even more crucial to manage these non-human privileges safely.
What Is Privileged Access?
Privileged access means special permissions given to users or systems that need to do important tasks. For example, a system admin who needs to update firewall settings or a service account that needs to connect to a company database.
This access must be carefully controlled. Too much access increases the chance of misuse, while too little access can slow down business work. PAM helps find the right balance, which allows smooth work without compromising security.
What Are Privileged Credentials?
Privileged credentials are the login details, like passwords, SSH keys, or tokens, that protect special accounts.
Here’s the scary part: if hackers get their hands on these credentials, they can log in as an admin and poke around your sensitive systems without anyone noticing. Forrester Research found that nearly 80% of data breaches happen because of stolen privileged credentials.
Remember the Target breach back in 2013? Attackers stole login details from one of Target’s vendors and used them to break into their internal systems. A good PAM system could have stopped that attack in its tracks.
How Does Privileged Access Management Work?
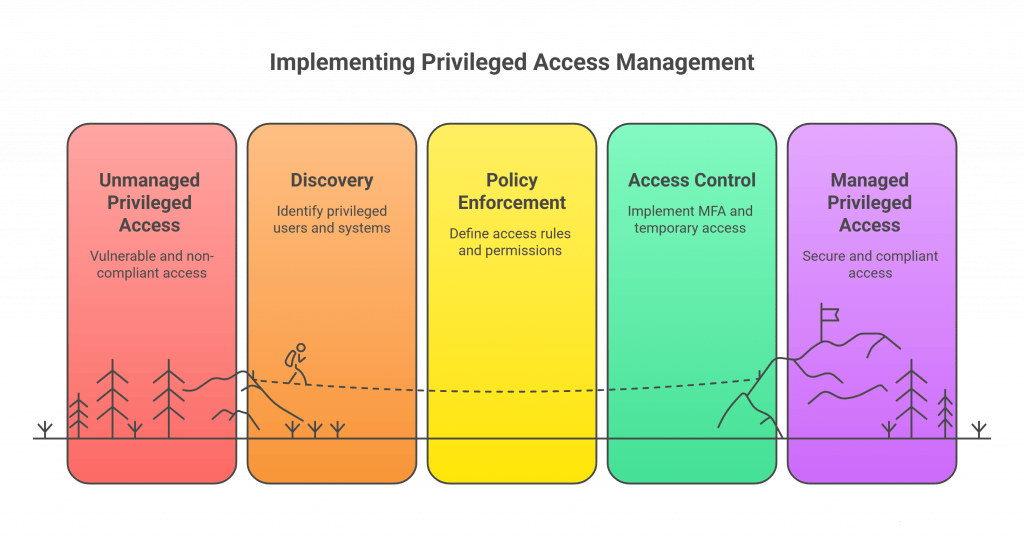
A PAM solution acts as both a gatekeeper and a detective. Here’s how it typically works:
- Discovery: First, it figures out which users, systems, and apps actually need special access.
- Policy Enforcement: Then it sets up clear rules – who gets access to what, and under what circumstances.
- Access Control: It adds extra security layers like multi-factor authentication and temporary access that expires when the job’s done.
- Session Monitoring: Every time someone uses privileged access, PAM records it and watches for anything suspicious.
- Auditing & Reporting: It keeps detailed logs that help you stay compliant with regulations like HIPAA, GDPR, and PCI DSS, and makes investigating security incidents much easier.
The bottom line? PAM keeps the hackers out while helping you meet your legal obligations, like HIPAA, GDPR, and PCI DSS.
Privileged Access Management Use Cases
PAM plays a key role in several cybersecurity scenarios:
1. Shrinking the Identity Attack Surface
Hackers love valid accounts because they let them blend in. PAM helps stop privilege creep and retires old or unused accounts, ensuring every identity in your system has a clear purpose and limit.
Using credential vaults and enforcing least-privilege access reduces lateral movement, the technique attackers use to spread across networks. PAM also supports a Zero Trust model, where every access request is verified, even inside the network.
2. Managing Identity Sprawl
With cloud apps, IoT devices, and AI integrations everywhere, most organizations now manage hundreds of privileged identities, many of them non-human.
PAM helps manage this sprawl by securely storing credentials, rotating them automatically, and tracking all privileged activity across users, devices, and bots.
3. Meeting Compliance Requirements
Regulations like HIPAA, GDPR, and PCI DSS require organizations to control who accesses sensitive information. PAM helps enforce these rules by granting limited privileges, maintaining audit trails, and ensuring every privileged action is traceable.
4. DevOps Secret Management
DevOps teams often use scripts, APIs, and automation tools that need access to servers and databases. Unfortunately, these credentials are sometimes stored in plain text or embedded in code.
PAM solutions store these secrets in a centralized vault, rotate them frequently, and ensure only authorized apps or users can access them. This keeps the DevOps pipeline both agile and secure.
Benefits of Privileged Access Management
Implementing PAM brings multiple benefits to organizations of all sizes:
- You get better security as it protects data against insider threats, credential theft, and also avoids the misuse of privileges.
- Your business stays compliant more easily as it simplifies audits and helps you meet standards like PCI DSS and GDPR.
- It lowers breach risks since least-privilege access limits the damage from compromised accounts.
- The access is centralized; thus, it saves IT teams’ time.
- It makes operations easier by automating password management, session tracking, and reporting.
Common Privilege Management Challenges
Organizations often struggle with managing who has access to what. Here are a few issues PAM helps solve:
Users often retain admin rights they no longer need. This privilege creep expands the attack surface. On the other hand, teams sometimes share admin credentials for convenience, making it hard to track who did what.
Ex-employees’ accounts are sometimes left active, giving attackers hidden entry points. Moreover, large companies have thousands of accounts, making manual oversight impossible.
Also, proving who accessed which system and why can be tough without proper PAM tools.
By implementing PAM best practices, organizations can tackle these challenges head-on.
Privileged Access Management Best Practices
The following best practices must be followed to make most out of your PAM system:
- Start by giving everyone only the access they actually need to do their job. Least privilege is important.
- Multi-factor authentication is another important thing while giving credentials, especially for admin accounts and anyone logging in remotely.
- Make sure you regularly change passwords and SSH keys. Leaving one credential active for a long time can welcome attackers.
- Record and keep an eye on all high-risk activities.
- Give temporary access to reduce long-term risk. For example, you can have a timeout feature for a session.
- Remove unused or duplicate privileges. Forgotten accounts are prime targets for attackers.
These steps work together to create a strong defense against attacks that target stolen credentials.
PAM vs IAM: What’s the Difference?
Identity and Access Management is a broader concept that manages digital identities for all users – employees, customers, and partners.
Privileged Access Management is a specialized branch of IAM that focuses specifically on accounts with elevated privileges, like system administrators or database managers.
| Aspect | IAM | PAM |
|---|---|---|
| Scope | All user identities | Only privileged users & accounts |
| Goal | Control general user access | Protect high-risk admin access |
| Tools | SSO, MFA, user provisioning | Password vaults, session recording |
| Use Case | Employee logins | IT admins, service accounts |
Suggested Read: IAM vs PAM: Key Differences, Use Cases & Best Practices
Conclusion
According to IBM’s Cost of a Data Breach Report, breaches caused by stolen credentials cost organizations an average of USD 4.67 million. When insiders misuse valid access, that number climbs even higher, nearly USD 4.92 million.
Privileged Access Management isn’t something you should ignore. It’s a practical, proven way to lock down your organization’s most powerful accounts, monitor every privileged action, and ensure compliance across your systems.
Mehlika Bathla is a passionate content writer who turns complex tech ideas into simple words. For over 4 years in the tech industry, she has crafted helpful content like technical documentation, user guides, UX content, website content, social media copies, and SEO-driven blogs. She is highly skilled in... Read more








