DDoS in Cyber Security: Complete Guide to Attack Types and Protection
The internet may look calm on the surface, but behind the scenes, it’s constantly under attack. One of the most common and damaging threats that websites and online services face today is the DDoS attack. It is abbreviated as Distributed Denial of Service.
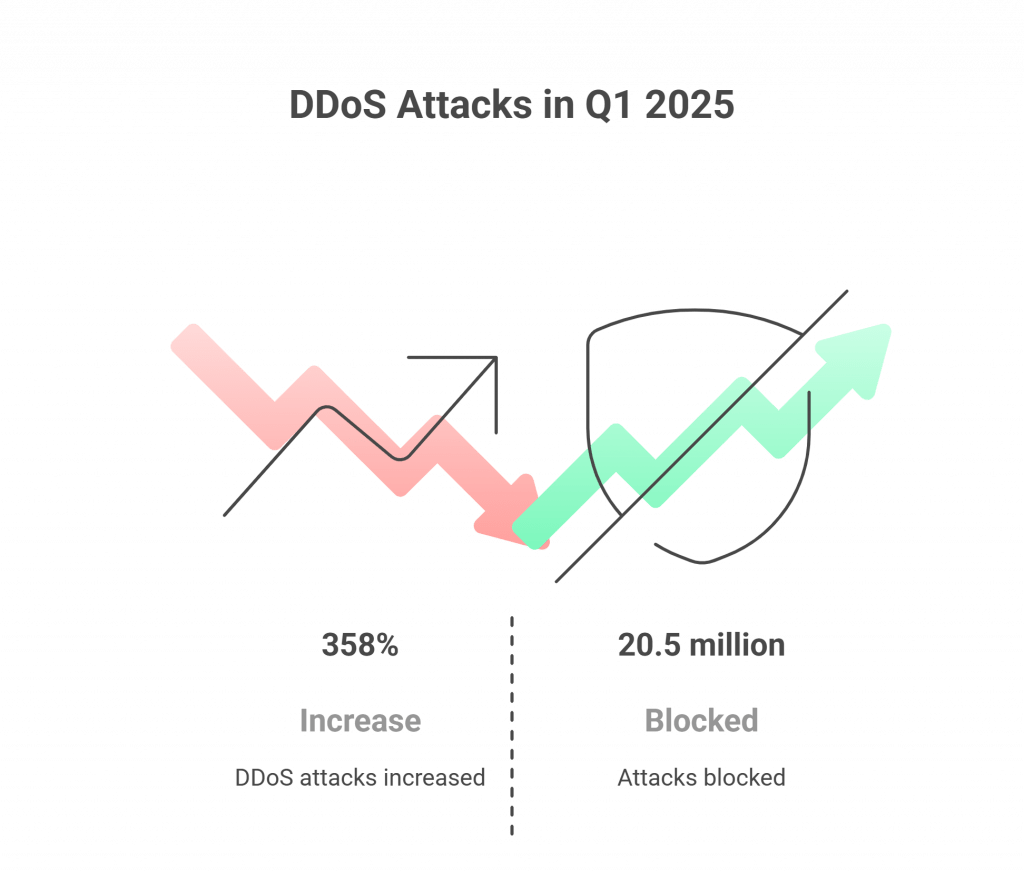
According to a recent cybersecurity report, DDoS attacks increased by 358% in Q1 2025, with over 20.5 million attacks blocked during this period. These numbers are proof of how serious and frequent such attacks have become. It has left no gaming servers, eCommerce sites, or corporate networks, and no one is completely safe.
This blog post will cover:
- What do DDoS attacks in cyber security mean?
- How DDoS attacks work?
- What can be done to stop them and more!
- Popular cybersecurity tools that could be of help and more
What is a DDoS attacks in cyber security?
A Distributed Denial of Service DDoS attack in cybersecurity occurs when a server or network is overwhelmed with massive traffic by a large number of compromised computers or devices, typically members of a botnet.
What’s the goal of DDoS attacks? To overwhelm the system with traffic to the extent that genuine users are unable to use it.
Put simply, you can just imagine that there are thousands of fake users trying to enter a shop simultaneously. These fake users prevent the entrance of real customers from entering the store. That’s exactly what a DDoS attack does to online services and websites.
Quick fact: The earliest documented Denial of Service (DoS) attack took place in 1974. David Dennis, a 13-year-old student at the University of Illinois Urbana-Champaign developed a program that crashed computers due to a fault in the PLATO system. The terminals also became unresponsive and had to be restarted which was the first move towards what we now call DDoS attacks.
DoS and DDoS Attack Difference
Both DoS and DDoS attacks in cybersecurity aim to disrupt online services, but the scale and method are quite different. Here’s a quick comparison to help you understand better:
| Aspect | DoS Attack | DDoS Attack |
|---|---|---|
| Abbreviated as | Denial of Service | Distributed Denial of Service |
| What’s the source? | Single computer or network | Multiple computers or devices (botnet) |
| Scalability? | Limited, small-scale disruption | Large-scale and harder to stop |
| Slow or Fast? | Slower, easier to detect | Faster, more complex |
| What’s the impact? | Temporary service slowdown | Complete service outage or crash |
| Any example? | One hacker floods a website | Thousands of infected systems attack at once |
How Does a DDoS Attack Work?
A DDoS attack follows a simple but powerful chain of events.
- Attacker: The attack begins when a cybercriminal sets up or rents a botnet. A botnet is a network of infected devices like computers, routers, or IoT gadgets.
- Botnet: These compromised devices are silently controlled by the attacker. When the attacker commands, they start sending massive amounts of traffic or requests to a specific website or server.
- Target Server: The target server receives more traffic than it can handle. As a result, it slows down, becomes unstable, or crashes completely, leaving real users locked out.
In essence, the attacker never directly touches the target; instead, they use thousands (sometimes millions) of devices to attack.
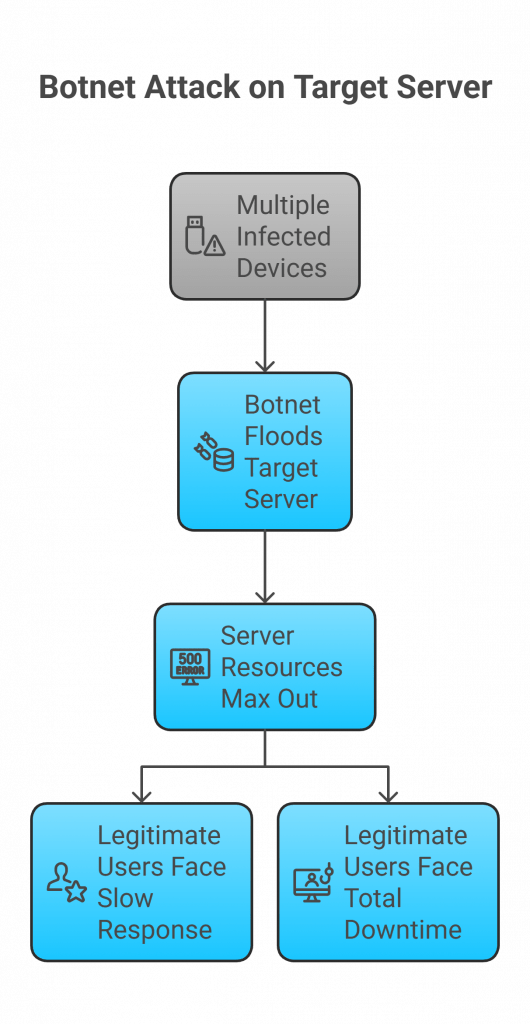
- Step 1: Attacker controls multiple infected devices (botnet).
- Step 2: Botnet floods the target server with fake traffic.
- Step 3: Server resources (CPU, bandwidth, memory) max out.
- Step 4: Legitimate users face slow response or total downtime.
Types of DDoS attacks in cyber security
Not all DDoS attacks work the same way. Hackers use different methods depending on what kind of disruption they want to cause and which part of the network they want to target. Let’s look at the main types of DDoS attacks every business should know.
1. Volume-Based or Volumetric Attacks
These are brute-force and the most frequent DDoS attacks. They carry out a huge amount of fake traffic on the target bandwidth until the system can no longer process any other requests.
Example: UDP floods or ICMP floods.
These attacks are calculated in bits per second (bps) and their main intention is to blocking the target internet pipeline.
2. Protocol Attacks
These attacks are attacks on the network layer (Layer 3 and Layer 4) of the OSI model. They do not overload the bandwidth but use vulnerabilities in data processing by network protocols.
Example: SYN floods and Ping of Death attacks.
These attacks use server resources such as firewalls and load balancers leaving them inaccessible to legitimate users.

Singularity Complete
Starting Price
$ 159.99
3. Application Layer Attacks
They are smarter and dangerous since they simulate normal user behavior. The intruder makes as many requests as possible to the application, such as logged-in pages, search forms, or payment portals. These further exhaust the web server’s processing power.
Interesting stat: Layer 7 DDoS attacks increased by 74% in Q1 2025 with a higher number of attacks focusing on APIs using large volumes of HTTP/HTTPS requests. A lot of these attacks were fuelled by huge botnets of IoT, which could easily be undetected and avoided.
4. Fragmentation Attacks
In this type, attackers send fragmented packets of data to the target system. When the target tries to reassemble these fragments, it gets overwhelmed and slows down, or even crashes.
Fragmentation attacks often bypass traditional security systems, which makes them particularly sneaky.
Famous DDoS Attacks
Over the years, several famous DDoS attacks have made headlines and caused massive disruptions across the internet. Here are a few major ones that show the real-world impact of this threat:
1. AWS Attack (2020)
Amazon Web Services (AWS) reported in February 2020 one of the most significant DDoS attacks in history, with the highest rate of 2.3 terabits per second. The hackers relied on hijacked CLDAP web servers to deliver huge data floods to AWS systems. Yet, AWS succeeded in mitigating and preventing the attack with its well-developed mitigation system, but it made clear how large modern DDoS attacks can be.
2. GitHub Attack (2018)
The famous software development system GitHub was also a victim of a DDoS that reached a peak of 1.35 Tbps. It was a brief yet very powerful attack that brought the site down, at least temporarily. By using the services of Akamai, which has DDoS protection services, GitHub managed to recover operations within a few minutes.
3. University of Minnesota (1999)
One of the first examples of DDoS attacks took place on July 22, 1999, when the University of Minnesota was attacked with the help of a tool called Trin00. The network of the university was flooded with huge data packets that were sent through approximately 114 infected computers. This led to a serious disruption of the network for more than 48 hours. The attack was one of the earliest massive DDoS attacks ever.
Why DDoS Attacks Are So Dangerous?
A DDoS attack might not steal your data directly, but it can bring your entire digital operation to a halt. Here’s how they can harm businesses of all sizes:
1. Financial Losses
When servers go down, websites stop functioning, and customers can’t make purchases or access services. This downtime leads to lost sales, productivity loss, and even SLA (Service Level Agreement) violations.
2. Operational Disruption
A strong DDoS attack can paralyze core operations, from internal communications to critical applications. Even short outages can cause chaos for teams, suppliers, and customers trying to access essential services.
3. Reputational Damage
Perhaps the most lasting impact is the loss of customer trust. When users repeatedly face downtime or poor performance, they often turn to competitors. A single large-scale attack can leave a permanent dent in a brand’s reputation.
How to Identify a DDoS Attack?
One of the biggest challenges with ddos attacks in cyber security is that they usually come without warning.
Most businesses realize something is wrong only when customers start complaining that the website is slow or unreachable. At first, it could look like a server glitch or hosting issue, but when investigated closely, it often reveals unusual spikes in traffic or server resource usage.
Here are a few common clues that signal a DDoS attack might be underway:
1. Unusual Traffic Patterns
If a single IP address is making too many requests in a short time, or you see sudden spikes in visits from one region, it’s a red flag.
You can set up automated alerts in tools like Loggly or Datadog to notify your IT team when traffic exceeds normal limits.
2. Frequent 503 Errors
A 503 Service Unavailable message means your server is overwhelmed. While occasional 503s can happen, a sudden flood of them indicates your system is being overloaded with fake requests.

Loggly
Starting Price
$ 948.00
3. Slow or Timed-Out Connections
If your ping requests start timing out or taking unusually long to respond, your bandwidth might be saturated. Global ping monitoring services can help detect this early by checking performance from multiple regions.
4. Internal Network Slowness
If employees notice a lag in internal apps or emails, it might be because your external traffic is eating up all your network resources.

Datadog
Starting Price
$ 15.00
How to Prevent a DDoS Attack?
While you can’t stop attackers from trying, you can prepare your systems to resist their attempts. Here are some practical and proven ways to prevent or reduce the impact of DDoS attacks in cybersecurity:
1. Take Quick Action
Time is everything. The faster you detect a DDoS attack, the less damage it can do.
Set up automated alerts that notify your network admins or security team the moment abnormal traffic is detected.

Sophos Firewall
Starting Price
Price on Request
2. Configure Firewalls and Routers
The initial measure you should take is your firewall and router set up. Ensure that your firewall security management software are updated with the latest security patches, plus rules that block out the fake or malformed traffic. Rate limiting is also a useful technique to limit the number of requests that a server receives over a period of time.

Check Point Next Generation Firewalls (NGFWs)
Starting Price
Price on Request
3. Use Artificial Intelligence
Complex DDoS patterns are usually missed by traditional security tools. This is where AI-based detection systems will be useful. AI has the ability to learn the normal behavior of the traffic in a short time and automatically block suspicious surges before they cause actual damage.

NGINX Plus
Starting Price
Price on Request
4. Secure IoT Devices
Today, most botnets are constructed by compromising IoT devices such as cameras, routers, and smart homes. To ensure that your devices do not join a botnet:
- Use strong, unique passwords
- Regularly update firmware
- Install trusted security software
5. Conduct Regular Risk Assessments
No system is perfect. Conducting frequent risk assessments and audits helps identify weak spots before attackers do. By understanding which servers or applications are most vulnerable, you can prioritize your defenses.

Azure Web Application Firewall
Starting Price
Price on Request
6. Use Smart Traffic Management
If you are under attack, try traffic differentiation-identify which requests are legitimate and which are not. Using Anycast networks, you can spread traffic across multiple distributed servers so that the load becomes easier to manage.
7. Enable Black Hole Routing (in Extreme Cases)
If the attack becomes too strong, administrators can temporarily reroute all incoming traffic to a black hole, effectively dropping both good and bad traffic. This is a last-resort measure, but it can help protect your infrastructure while you regroup.
8. Deploy Web Application Firewalls (WAF)
A Web Application Firewall acts as a shield between the internet and your servers. It filters out malicious traffic targeting the application layer (Layer 7), where many DDoS attacks strike today.
Conclusion
DDoS attacks in cybersecurity are no longer uncommon or exclusive to big companies. Small enterprises, online stores, internet games, and even ordinary websites may fall victim.
The worst part of these attacks is that anybody with basic technical skills can hire a botnet online on the dark web and carry out a tremendous attack in minutes. Being ready with intelligent monitoring, firewalls, AI-driven systems, and DDoS protection service can help you avoid these attacks.
The better you understand DDoS attacks and how to stop them, the stronger your online protection will become.
FAQs
What makes it difficult to prevent a DDoS attack?
The volume and distribution of the attack itself is the greatest challenge. DDoS attacks are initiated by thousands of infected devices distributed all over the world which makes it difficult to detect fake traffic and real users on the fly.
What is the full form of DDoS attack?
DDoS stands for Distributed Denial of Service. It is a cyber-attack through which several systems bombard a target server or a network with a lot of traffic to crash or reduce its speed.
How to stop DDoS attacks on game servers?
Install specific gaming DDoS defense software or proxy servers that are capable of handling overload. Cloudflare Spectrum and AWS Shield are commonly used software to secure gaming servers against volumetric attacks.
How to stop a DDoS attack on your router?
Upgrade router software, turn off remote access, and change default passwords. You also have the option of turning rate limiting on and setting firewall rules to block suspicious IPs. In severe cases, refer to your ISP to help mitigate the attack.
How to stop a DDoS attack on your IP?
When you are targeted by your IP address, change your IP temporarily or request your ISP to assign you a new dynamic IP address. You can also use a DDoS protection service or VPN to conceal your actual IP and to divert attack traffic.
Mehlika Bathla is a passionate content writer who turns complex tech ideas into simple words. For over 4 years in the tech industry, she has crafted helpful content like technical documentation, user guides, UX content, website content, social media copies, and SEO-driven blogs. She is highly skilled in... Read more




























