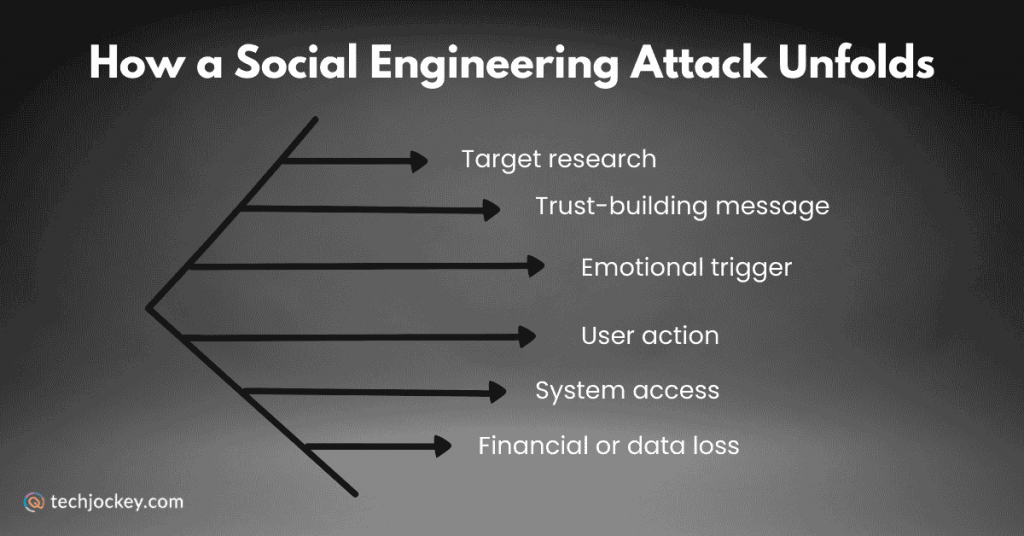
Almost everyone must have once gotten a message that looked like it came from a friend, your bank, or a company you trust. It could be that it asked you to click a link, update a password, or share a code that popped up on your phone. It might have felt just like a normal and safe message to you.
But what if that message wasn’t from who you think it was? That simple moment of trust, a click or reply, is often exactly what cybercriminals are waiting for. And that’s what social engineering in cybersecurity is.
Not only do firewalls and encryption come under ‘cybersecurity,’ but also fighting against social engineering. It doesn’t try to break into a system with code or brute force. Instead, it tricks people because the easiest way into many systems is through the people who use them.
What Is Social Engineering in Cybersecurity?
Social engineering, in simple words, is when an attacker tricks someone to do something that benefits the attacker. It’s not similar to hacking software; instead, it’s hacking human judgment. It could be via email, phone, text, or in person. The attacker aims to make you share something you shouldn’t, like login details, account numbers, personal information, or access codes.
For businesses, the damage can be huge. For individuals, it can be life-changing.
Common Social Engineering Techniques
Here are some familiar ways attackers trick people:
Phishing
This is the most common social engineering method. It’s when someone sends a message, often an email, pretending to be from a trusted source. The message might have a link or attachment that looks real. Many phishing messages imitate banks, delivery companies, or even coworkers. People click a link and then enter sensitive information without realizing they’re being tricked.
According to recent data, about 91% of cyberattacks begin with a phishing email. This shows how popular and effective this method remains.
Suggested Read: What Is Phishing: Types, Examples & Prevention Guide
Pretexting
In pretexting, the attacker invents a story to gain trust. They might pretend to be from IT support, a government agency, or a vendor. They ask for information that seems reasonable, like login credentials, but it’s all fake and needs to be ignored or confirmed with the sender.
Vishing and Smishing
These are voice and SMS (text message) versions of phishing. A scam phone call pretending to be from your bank, asking you to verify an ‘urgent’ issue, can make anyone jump. In the same way, a text asking you to click a link to confirm delivery details can seem normal until malware or identity theft follows.
Suggested Read: Phishing vs Vishing vs Smishing – Key Differences & Protection Tips
Baiting
This is like leaving a tempting item in plain sight. It might be a USB stick labelled ‘Bonus Payroll Info 2025’ left in an office break room. Someone plugs it in out of curiosity, and loads malware onto their system.
Impersonation on Social Media
Attackers pretend to be someone you know or someone in authority. They send a direct message asking you to take an urgent action. Because they look real, people often comply.
None of these requires advanced hacking skills. They require patience, psychology, and the ability to make something look familiar or urgent.
How Big Is the Problem?
Social engineering isn’t some fringe issue anymore. The numbers show that it’s widespread and growing:
A 2025 report found that about 80% of organizations listed social engineering as the biggest human-related risk they face in cybersecurity.
Another set of recent statistics shows that over 75% of organizations experienced a successful social engineering breach, and that almost half of social engineering attacks involve pretexting or impersonation.
These statistics make it clear that social engineering is not rare; it’s a central way attackers are getting in.
Even for individuals, the numbers are eye-opening. A huge number of scams, from fake job offers to banking messages, use social engineering to get people to reveal sensitive information or act before thinking.
Real Life Social Engineering Examples
Here are a few simple scenarios that show how social engineering might happen:
1. A known person’s hacked email:
You get an email from someone you know. The email says they’re in a meeting and asks you to transfer money or share a code. You trust the sender because you know them. It turns out, their account was hacked, and now the attacker is using it to get money from their contacts.
2. Fake bank alert:
You receive a text message that looks exactly like one from your bank. It says your account will be locked unless you confirm details. The website link looks legitimate. You enter your username and password, but it was a fake site, and now your account is compromised.
3. Urgent work message:
A phone call to an employee from someone claiming to be from the IT team asks for a password reset. The employee wants to help quickly and shares credentials, not realizing the caller was a scammer doing voice impersonation. These happen almost every day to individuals and businesses of all sizes.
The Damage of Falling for Social Engineering
When a social engineering attack succeeds, the fallout can be big. Here’s what can go wrong:
- Stolen credentials: Hackers can take over accounts and systems. A few reports indicate that credential theft surged more than 160% in 2025. It’s clear that attackers are getting access to login information on a very large scale.
- Monetary loss: Attackers can use accounts illegally and can make unauthorized purchases or commit identity theft.
- Data breach: In case attackers get access to an employee’s account, then there are high chances of business data being accessed.
- Brand trust damage: This is the biggest social engineering attack risk to businesses. Customers may lose trust if their information is exposed.
It’s even more devastating for small companies, losing key accounts or data. Even individuals may face financial hardship or long-term identity problems.
How to Protect from Social Engineering?
You don’t need to be a cybersecurity expert to reduce risk. Here are practical ways to stay safer:
- You must first understand what scams look like. Learning the common tricks, like fake URLs or odd greetings, can help you spot threats.
- Take a moment before reacting. If something seems urgent, pause and verify it from a separate source. For example, call your bank using a known number.
- Be careful with links and attachments. If an email promises something unusual or comes from an address you barely recognize, think twice before clicking.
- For businesses, having a second step, like calling a person to confirm a request, can stop impersonation attacks.
- Businesses that practise phishing simulations and awareness training see fewer successful attacks. Continual learning helps people recognize tricks before they fall for them.
- Things like multi-factor authentication make it harder for attackers to use stolen credentials.
Nowadays, passwordless authentication is gaining popularity because it removes passwords entirely, and solutions like PreAuth help stop social engineering attacks by making stolen credentials useless.
How Cybersecurity Software Helps Prevent Social Engineering?
It’s good to be aware, but even careful humans could also make mistakes on busy days. And that’s where you need a good cybersecurity software that keeps you out of the fear of being attacked, preventing social engineering in cybersecurity.
Here we go with discussing the right tools that can help reduce social engineering risks:
1. Email and phishing protection
Complex email security systems scan incoming emails to detect unreal sender names, suspicious links, and common scam patterns. Several such platforms, such as Proofpoint and Microsoft Defender, are common to block phishing email before it even gets to inboxes.
2. Link and website filtering
The cybersecurity tools could alert users when attempting to open unverified or malicious sites. Even when an individual clicks a phishing link, the software can block loading the page or leave a clear notification that the site is risky. Malicious links can be minimized by using solutions such as Cisco Secure Email and Cloudflare Gateway.

Microsoft Defender
Starting Price
₹ 170.00 excl. GST
3. Identity and access protection
Identity-focused cybersecurity software helps ensure stolen credentials alone are not enough for attackers. Tools such as Okta and Microsoft Entra ID provide an extra layer for verification and can also monitor unusual login behavior.

Okta
Starting Price
$ 2.00
4. Endpoint security
In case a person downloads an infected attachment or connects the USB device that is infected, endpoint protection tools will identify and prevent the attack. The CrowdStrike Falcon software is used to prevent malware and suspicious behavior before it can propagate across the systems.

CrowdStrike Falcon Endpoint Security
Starting Price
$ 59.99
5. User behavior monitoring
Some sophisticated cybersecurity platforms can identify suspicious behavior using AI, including data downloads or logins that occur in an unusual place. This enables the security teams to be prompt in responding to cases where an account has been hacked using social engineering.
For businesses, cybersecurity software could save crucial data. It doesn’t replace training or awareness, but it significantly reduces damage when someone slips up. For individuals, even basic security tools can block many common social engineering attacks before they cause harm.
What the Future Holds?
As our lives become more connected with cloud services, mobile devices, and digital communication, social engineering in cybersecurity will be continued till we stop using tech.
Cybercriminals are just sitting and experimenting with new black hat techniques to make their scams feel more real and urgent.
But the good news is that awareness and cautious habits can make a huge difference. You may not stop every attack, but you can avoid the simple ones that make up the vast majority of successful social engineering schemes.
The more people understand the tricks, the smaller the advantage attackers have.
Conclusion
Social engineering in cybersecurity isn’t about technology flaws. It’s about human behaviour. It’s about how attackers use trust, urgency, and familiarity to trick people into giving away information or access. And because people are part of every system, social engineering will continue to be one of the most effective ways attackers achieve their goals.
The main agenda of this article is not to make you live in fear, but to make you prepared, aware, and thoughtful about what you share and how you respond.
After all, the strongest security isn’t just digital. It starts with people.
Mehlika Bathla is a passionate content writer who turns complex tech ideas into simple words. For over 4 years in the tech industry, she has crafted helpful content like technical documentation, user guides, UX content, website content, social media copies, and SEO-driven blogs. She is highly skilled in... Read more