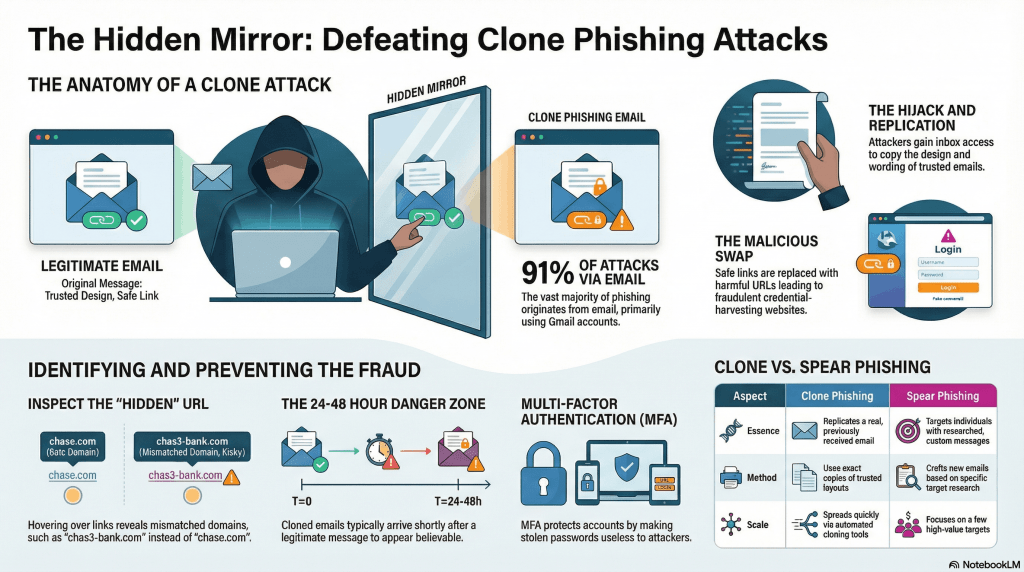
Clone phishing is one of the most dangerous email threats targeting businesses today. Cybercriminals, in order to carry it out, make copies of genuine messages and embed malicious links and attachments in them to trick the recipients into revealing confidential information.
If statistics are to be believed, 91% of phishing attacks are conducted via email, with 91% of these originating from Gmail accounts (an IdentityTheft.org report). It is imperative thus you have an in-depth understanding of the said threat and its workings, so any attempt made at striking you fall flat. Let’s get into it then, shall we?
What is Clone Phishing?
Clone phishing is an email-based phishing attack, wherein attackers copy an authentic email that a recipient previously received and make minor changes to it by inserting fraudulent links or attachments. This is done to either deliver malware or harvest sensitive credentials.
Since these copies resemble familiar correspondence, recipients easily trust them, making the attack successful. A classic clone phishing example would be employees receiving duplicated vendor invoices. The legitimate version would obviously be arriving first, followed by the malicious duplicate requesting payment details.

SimpleDMARC
Starting Price
$ 99.00
How Does a Clone Phishing Attack Work?
A clone phishing attack works by duplicating a legitimate email and replacing safe links or attachments with malicious ones.
Clone phishing follows an extremely simple sequence that increases its success rates. First, attackers get access to a victim’s inbox. This is often done through a data breach or malware. Once they get proper access, they search the inbox for genuine emails from trusted sources like banks or colleagues.
Having found these messages, they begin copying the design, wording, and sender details to make the email look real. Then they make one key change, i.e., replacing safe links with harmful ones that lead to fake websites. These sites are designed to look like the real thing, so when victims click and enter their details, attackers steal their credentials.
What makes this worse is that cybercriminals use easy-to-get tools that automate the process, allowing them to send thousands of cloned emails quickly.

KDMARC
Starting Price
Price on Request
What are Common Clone Phishing Tactics?
Attackers employ reliable clone phishing tactics proven to bypass defenses. One common trick is cloning shared document notifications. For example, victims receive what looks like a Google Drive link for a file update, but the link actually installs malware.
Financial alerts are another favorite. Cybercriminals often copy bank statements or wire transfer confirmations and send them with fake verification links. Google Pay notifications are frequently cloned using the same approach.
Delivery confirmation emails also get abused, especially during holiday seasons. Attackers copy legitimate Blue Dart or Delhivery messages and add problem-resolution links that lead to fake tracking portals designed to steal login details.
They do not spare corporate IT messages either, as they clone software update notifications and turn them into malware delivery tools.
Suggested Read: What is Phishing – Meaning, Types & Attacks
What Does a Clone Phishing Email Look Like?
Clone phishing emails perfectly replicate genuine correspondence. From corporate logos, color schemes, fonts, and signature blocks to display names, these copy everything as precisely as possible.
For example, an authentic Amazon order confirmation like ‘Order #1234567890 Shipped: Track Package’ is duplicated. The message body looks the same too, with only small changes, such as turning ‘View order’ into ‘Update payment method’.
Links in these emails look reliable at first, but hovering over them reveals the truth. A real link might show paytm.com, while a fake one redirects to paytm-secure-login.in. Attachments also look familiar, using names like ‘Invoice_January.pdf‘, but they often hide harmful files.
To make matters worse, attackers design these emails to look perfect on mobile devices. Every logo, color, and layout matches the original, making it hard for even careful users to spot the difference. This visual authenticity is what makes clone phishing so dangerous.

Trend Micro Email Security
Starting Price
Price on Request
How to Recognize a Clone Phishing Email?
Identifying clone phishing involves a range of technical details. Start by checking the sender’s email address. Genuine companies use domains like @company.com, while fake ones often add extra words, such as @company-support.net. These small mismatches are a common giveaway.
Next, hover over every link before clicking. Real URLs match the company’s domain exactly, but cloned emails often hide misspellings or extra subdomains. For example, a real link might show chase.com, while a fake one uses chas3-bank.com. Attackers often build fake websites behind these links to steal your information.
Attachments are another red flag. Banks and financial institutions never send executable files (.exe) by email. If you see unexpected file types, treat them as suspicious; modern security tools usually block these automatically.
Timing can also be a clue. Cloned emails often arrive within 24-48 hours of a genuine message on the same topic, making them seem believable. Finally, if you are unsure, contact the sender through a verified phone number or official website.

Sophos Phish Threat
Starting Price
Price on Request
How to Prevent Clone Phishing Attacks?
Start with employee education. Teach your staff how to spot duplicate emails and use real-world examples during awareness sessions.
Next, deploy advanced email security software that compare incoming messages to known legitimate ones. These systems can block suspicious emails before they reach inboxes. Adding multi-factor authentication is another smart move, as it makes stolen passwords useless even if someone falls for a phishing attempt.
Keep all software updated. Modern browsers often block fake websites automatically, reducing risk. Regular phishing simulations also help. Companies that run these drills can bring down the success rates significantly.
Finally, set up clear reporting procedures. If an attack is suspected, quick isolation prevents hackers from moving deeper into your network. Acting fast basically is crucial to minimizing damage.
Suggested Read: Phishing vs Vishing vs Smishing – Differences & Examples

GoDMARC
Starting Price
Price on Request
Clone Phishing vs Spear Phishing: Know the Difference
People often get confused between clone phishing and spear phishing, but the two significantly differ from each other. Here’s how…
| Aspect | Clone Phishing | Spear Phishing |
|---|---|---|
| Essence | Copies real emails/websites with malicious changes | Targets individuals with custom messages, no copying |
| Method | Uses exact replicas of trusted messages | Crafts new emails from research on targets |
| Examples | Leading clone phishing examples include copied bank alerts or shared docs | Personal details in emails to executives |
| Scale | Spreads via reused clones | Focuses on few high-value targets |
| Tech Used | Clone a website for phishing to mimic login pages | Generic fake sites, less exact copying |
Conclusion
Clone phishing in cybersecurity thus is as real a threat as it gets. Organizations across the globe should invest in advanced email security tools and train their employees at the same time to recognize suspicious messages and stop attacks before they cause damage.
If you need any help in procuring them tools, the likes of Trend Micro Email Security, Proofpoint Aegis, Avanan, SimpleDMARC and more, give Techjockey team a call today itself.
Yashika Aneja is a Senior Content Writer at Techjockey, with over 5 years of experience in content creation and management. From writing about normal everyday affairs to profound fact-based stories on wide-ranging themes, including environment, technology, education, politics, social media, travel, lifestyle so on and so forth, she... Read more





























