What Is a Network Intrusion Detection System? Types, Tools & NIDS vs HIDS
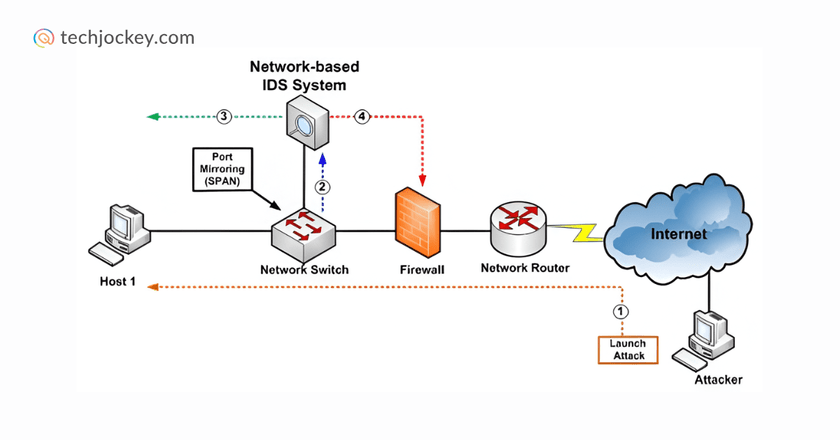
In today’s digital era, networks power everything from emails and payments to business operations. Traditional security tools are inadequate because cyberattacks are becoming more intelligent and more focused. It is necessary to monitor the network continuously.
A Network Intrusion Detection System, or NIDS, is a system that continuously monitors network traffic in order to detect suspicious traffic. This blog describes the concept of NIDS, its functionality, and its importance to current network security.
What Is a Network Intrusion Detection System (NIDS)?
A Network Intrusion Detection System (NIDS) refers to a security tool that is involved in monitoring network traffic in order to detect potential suspicious or malicious activities. It is mainly directed at their identification of potential danger, malware delivery, or hacking, before it becomes too late.
NIDS work by analyzing data packets passing through a network and alerting administrators when they appear suspicious. NIDS does not automatically block traffic, unlike intrusion detection and prevention systems. It is aimed at detection and alerting.
NIDS is a security tool in a defense-in-depth approach, which involves firewalls and other security applications in order to improve the overall visibility and security of a network.
Why Network Intrusion Detection Systems Are Important?
The reason why network intrusion detection systems are important is that they assist in detecting network attacks at an early stage. NIDS helps to avoid major damage as suspicious traffic can be detected fast. It also enhances the visibility of the entire network by showing abnormal or unauthorized/unlike behavior.
The other important advantage of NIDS is the ability to respond more quickly to possible security attacks. Early warnings enable the IT teams to respond before it is too late. Also, NIDS can assist in compliance and auditing and aid in the protection of sensitive personal, financial, and business information.
Suggested Read:What Is Intrusion Prevention System (IPS) – Types, Features & Benefits
How a Network Intrusion Detection System Identifies Attacks?
When considering the effectiveness of a Network Intrusion Detection System, we need to know how the system operates behind the scenes. NIDS continues to work at all times without interfering with the day-to-day operations. It scans network traffic and examines data based on smart detection techniques, and informs administrators about suspicious or malicious activity at the earliest stage possible.
- Signature-Based Detection: This approach generates a comparison between network traffic and a known attack signature and a predetermined pattern. An alert is raised when a match has been found. It works very well on known threats, but fails to work in new attacks or zero-day attacks.
- Anomaly-Based Detection: Anomaly detection involves the establishment of a normal network behavioral background and observing the network traffic activity for abnormal deviations. It assists in identifying new and unfamiliar attacks, yet it creates false alarms when normal activity is not regarded as normal.
- Hybrid Detection: Hybrid detectors represent signature-based and anomaly-based detectors. In the current NIDS, it initially identifies the threat through signatures and later recognizes unknown attacks by analyzing the behavior to enhance the accuracy and minimize the false alerts.
- Other Detection Techniques: Protocol analysis is used to identify the breach or abuse of network protocols, whereas heuristic analysis reveals the suspicious behaviour patterns associated with attacks. The techniques are productive in the detection of threats that are difficult or dynamic, as compared to the traditional techniques.
NIDS vs HIDS: Which Intrusion Detection System Is Better?
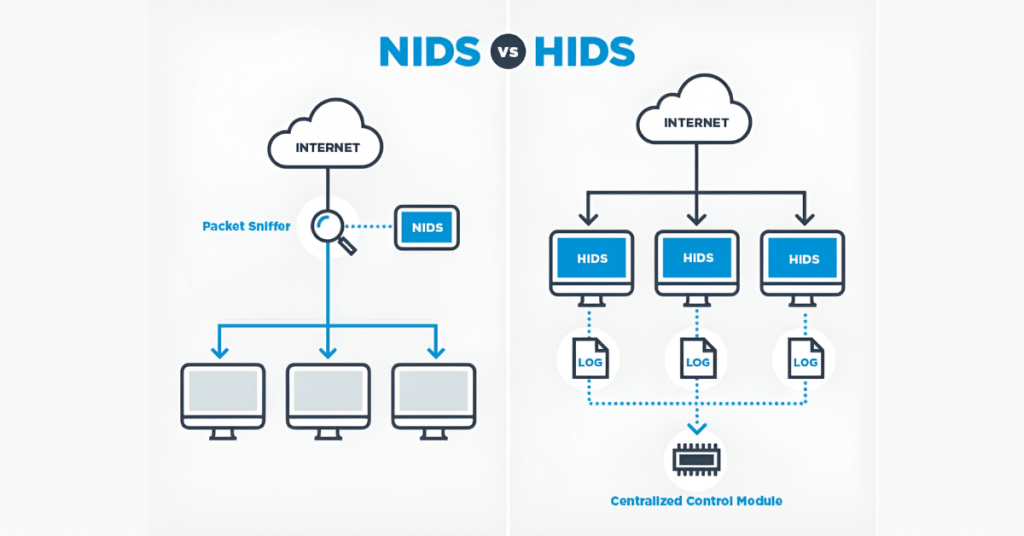
Host-based systems track logs, files, and activities in individual devices, whereas network-based systems monitor overall traffic. They both fall under Intrusion Detection Systems. The table below outlines the differences between NIDS and HIDS in major areas that allow you to learn more about their functions, scope, and general implementation in network security solutions.
| Feature | NIDS | HIDS |
|---|---|---|
| Monitoring scope | Monitors traffic across the entire network | Monitors activity on a single system |
| Deployment | Installed at gateways or network segments | Installed directly on individual devices |
| Data analyzed | Network packets and traffic patterns | System logs, files, and user actions |
| Threat focus | Detects network-wide attacks | Detects host-specific threats |
| Visibility | Limited insight into internal system changes | Full visibility of system activities |
| Resource usage | Uses network resources | Uses host system resources |
| Best suited for | Large networks and traffic monitoring | Servers and critical endpoints |
Core Components of a Network Intrusion Detection System
A Network Intrusion Detection System consists of some important parts that collaborate in order to track, analyze, and report the suspect network activity.
- Sensors and traffic collectors: These are used to capture network traffic at various points in the network and transmit data to be inspected and analyzed.
- Analysis engines: Analysis engines analyze the collected traffic to determine suspicious patterns or abnormal behavior by using detection methods.
- Detection rules and models: These are the rules and models that the system is supposed to be searching, such as known attack signatures and behavior-based patterns.
- Alerting mechanisms: The alerts are produced when a threat is detected to warn the administrators to act fast.
- Management and reporting dashboards: Dashboards allow centralized exposure, logs, and reports to assist in monitoring security occurrences and support auditing.
Key Features of an Effective NIDS
A good Network Intrusion Detection System has fundamental features that assist organizations in identifying threats and controlling network security solutions efficiently.
- Real-time monitoring: This is applied in the process of detecting suspicious traffic on the network in real-time.
- Accurate threat detection: Alerts on the actual threats and minimizes the false alarms.
- Low false positive rates: Help security teams work on actual threats rather than harmless activity.
- Scalability: Scales simply with the expansion of the network with no loss of performance.
- Integration with SIEM tools: Forwards information on shares to security tools to improve analysis and reaction.
- Custom rule creation: Can be used to create custom detection according to security requirements.
- Detailed logging and reporting: Keeps proper records to be investigated, audited, and met.
What Technologies Can a Network Intrusion Detection System Monitor?
A network-based intrusion detection system can be used to track various technologies within the network to detect security threats and malicious activity.
- Network Protocols: The protocols supported by NIDS are TCP/IP, HTTP, FTP, DNS, SMTP, and SNMP. It can detect the misuse, abnormal traffic patterns, and efforts to attack protocol vulnerabilities by analyzing protocol behavior.
- Network Devices: NIDS tracks the activity of routers, switches, and firewalls. It will help in detecting infiltration, dangerous traffic, and unusual configuration changes that might indicate a breach of data.
- Applications: Applications such as web servers, email servers, and databases are tracked for abnormal traffic. NIDS are able to detect any attempt at accessing confidential information or other malicious activities performed by applications.
- Operating Systems: When deployed, malware or unauthorized access can be detected by examining the traffic on the OS-level network and noticing any attempts to use the system vulnerability or malicious behavior.
- Wireless Networks: Wireless traffic can be monitored using NIDS to detect rogue access points, unauthorized connections, and denial-of-service attacks against wireless networks.
How to Deploy a Network Intrusion Detection System?
The deployment of a Network Intrusion Detection System must be strategically on exit gates or on important points of the network to track the traffic. Depending on the control and scalability requirements, organizations may use on-premises or cloud deployment. It is important to be properly configured to prevent performance problems, handle encrypted traffic, and integrate easily with current security tools.
Key Challenges and Limitations of NIDS in Cybersecurity
- Large traffic volumes: When the network traffic is high, it will be hard to monitor the network, and this will interfere with the accuracy of detection.
- False positives and alert fatigue: The high volume of security alerts activated will flood security teams, and real threat alerts will be slowed down.
- Limited visibility into encrypted traffic: Encrypted information can decrease the capacity of the system to scan the content of packets efficiently.
- Resource and expertise requirements: NIDS will need qualified human resources and system resources to be configured and monitored properly.
- Adapting to evolving attack techniques: The ever-evolving cyber threats need to be updated and tuned on a regular basis.
Top 5 Network Intrusion Detection Tools
| Tool | Key Strengths | Best Used For |
|---|---|---|
| Snort | Real-time traffic analysis, packet sniffing and logging, strong rule support | Detecting known network attacks |
| Suricata | High performance, multi-threading, GPU acceleration, deep packet inspection | High-speed and large networks |
| Zeek (Bro) | Behavioral analysis, detailed traffic logging, threat detection | Detecting stealthy and advanced threats |
| Security Onion | Combines Snort, Suricata, and Zeek for centralized monitoring | Enterprise-level security monitoring |
| OSSEC | Log monitoring, file integrity checks, rootkit detection | Endpoint and system-level security |
Who Is Network Intrusion Detection For?
NIDS applies to both large and small organizations that have to monitor and defend the network against cyber threats. Government agencies, academic institutions, and businesses that deal with sensitive information generally use it extensively.
NIDS is used by network administrators, IT teams, and security professionals to identify threats, investigate incidents, and ensure rigid compliance mandates in controlled sectors such as healthcare and finance.
How Network Intrusion Detection Systems Are Evolving?
The future of Network Intrusion Detection focuses on AI-driven detection, automated threat response, and cloud native solutions. Systems will learn normal behavior, detect complex attacks, respond instantly to threats, and use behavioral analysis to identify advanced and hidden cyber risks more accurately and efficiently.
Conclusion
Network Intrusion Detection Systems play a critical role in the protection of the current networks against the continuously evolving cyber attacks.
NIDS will help organizations detect attacks early in the network traffic by monitoring network traffic, detecting suspicious activity, and reducing the potential damage. It is an essential element of the sophisticated cybersecurity plan as it allows taking proactive security actions.
When combined with other security tools and best practices, NIDS strengthens overall network defenses and improves visibility across the infrastructure. Due to the continuously evolving and advanced cyber-threats, making investments in efficient intrusion detection is no longer a choice but a necessity.
If you want to learn more or need help choosing the right solution, reach out to Techjockey for expert guidance and detailed information.
FAQs
What is a network intrusion detection system?
A network intrusion detection system tracks network traffic and sends a notification to the teams in case of suspicious or dangerous activity.
What are the 4 types of intrusion detection systems
These four are network-based, signature-based, host-based, and anomaly-based intrusion detection systems.
What is an example of a NIDS?
Snort is a common example of a network intrusion detection tool that can be used to monitor and analyze network traffic.
What are NIDS used for?
NIDS are used to detect hacks, malware attacks, suspicious traffic, and other security threats on networks.
What are the benefits of using a NIDS?
NIDS enhances security, as it detects threats early, improves network visibility, and assists the teams in detecting and responding to attacks in a quick manner.
Is NIDS a firewall?
No, NIDS is not a firewall. It identifies and warns of threats, but without blocking traffic automatically.
What type of control is NIDS?
NIDS is a detective security control that identifies and reports suspicious network activity for further action.
Can NIDS detect zero-day exploits?
Anomaly-based NIDS are capable of detecting zero-day attacks because they can detect abnormal network traffic.
Sweety Sharma is a skilled content writer with expertise in crafting engaging content across various platforms, including websites and social media. Since 2018, she has written extensively on topics such as cryptocurrencies, stocks, nutrition, investment, technology, real estate, marketing, and many more. During her journey, Sweety has improved... Read more




























