‘The global losses due to cybercrime are estimated to hit approximately 10.5 trillion USD per year in 2025, and by 2029, the losses may reach 15.63 trillion USD if the trends remain the same.’
As the number of cyberattacks grows, the security teams not only require visibility but also speed, precision, and coordinated incident response. That is where SOAR and SIEM come in. Although they are both critical to cybersecurity, they have different purposes and functions at different levels of the security stack.
SOAR emphasizes the automation and orchestration of incident response. On the other hand, SIEM focuses on gathering, detecting, and analyzing security data throughout the organization.
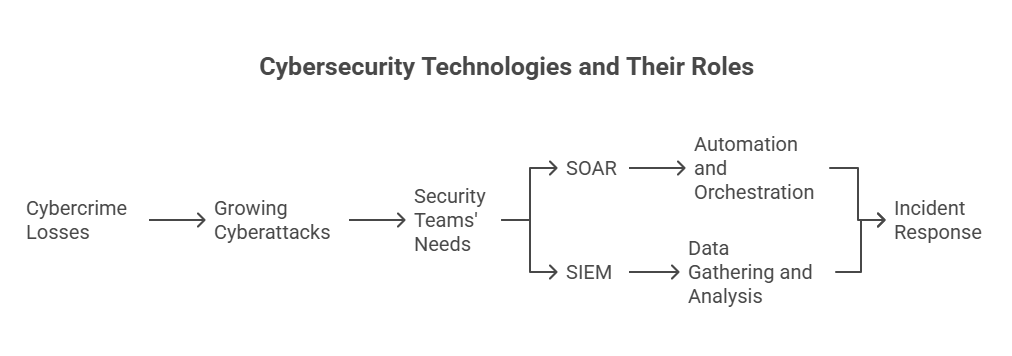
To see why security operations centers need both, it is first important to know how each technology works.
What is SOAR & How It Works?
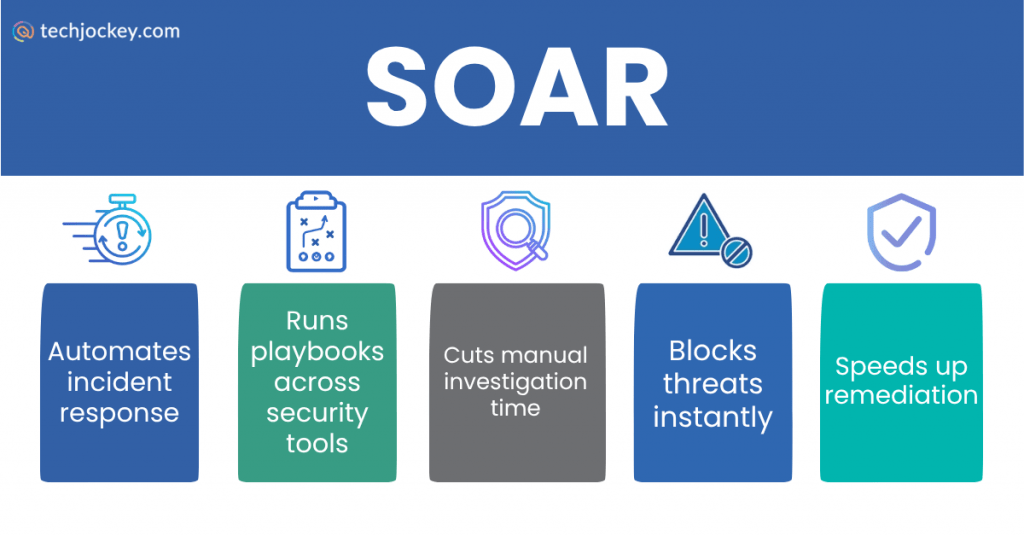
SOAR, which is also known as Security Orchestration, Automation, and Response, is a cybersecurity solution that is intended to simplify and automate incident response. It integrates various security tools, threat intelligence sources, and workflows, so that any threat alert is investigated and remediated with limited human intervention.
A daily life example for SOAR could be, like a smart home that detects smoke and automatically turns off the gas, opens doors, and calls the fire department without waiting for you.
How SOAR Works:
- Collects security alerts from various tools
- Automatically enriches alerts using threat intelligence sources
- Triggers predefined playbooks to respond to incidents
- Automates repetitive tasks such as IP blocking, user isolation, or ticket creation
- Allows analysts to approve or override actions when needed
SOAR reduces alert fatigue, speeds up investigation, and helps security teams focus on high-priority threats instead of drowning in manual processes.
What is SIEM & How It Works?
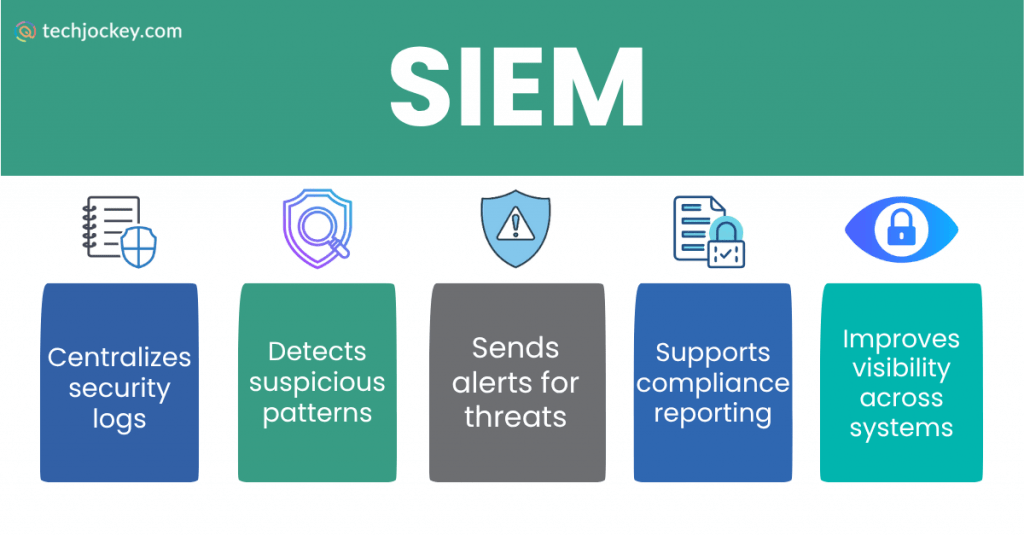
SIEM, which is abbreviated as Security Information and Event Management, is a platform that gathers and analyzes security log information in order to identify early threats. It provides visibility of organizations over networks, applications, endpoints, cloud services, and user activities.
SIEM can be related to a CCTV control room that watches every camera in the city to spot anything suspicious before something bad happens.
How SIEM Works:
- Collects logs and event data from all security and IT systems
- Correlates and analyzes data to identify suspicious patterns
- Uses rules and behavioral analytics to detect threats
- Generates alerts for potential security incidents
- Provides dashboards and reports for compliance and auditing
SIEM Platform acts as the eyes and brain of the SOC, enabling teams to detect anomalies before they evolve into major breaches.
SOAR vs SIEM – Key Feature Differences
| Feature | SOAR | SIEM |
|---|---|---|
| Primary Objective | Automates and orchestrates incident response for faster remediation. | Detects security threats through log collection, correlation, and analysis. |
| Core Function | Runs automated playbooks to respond to threats with minimal human input. | Acts as centralized visibility layer for all logs and events across IT systems. |
| Data Inputs | Ingests enriched alerts from SIEM, EDR, XDR, email security, cloud tools, etc. | Collects raw logs from servers, endpoints, networks, apps, cloud, IAM, etc. |
| Alert Handling | Prioritizes alerts using severity, threat intel, and playbook logic; reduces noise. | Generates alerts based on rules and behavior analytics; requires manual tuning. |
| Incident Response | Performs automated actions like blocking IPs, isolating endpoints, disabling accounts. | Notifies analysts about suspicious events but does not automatically remediate. |
| Automation | High automation using standardized playbooks for triage, containment, and remediation. | Limited or no automation; focused mainly on detection and correlation. |
| Threat Intelligence Usage | Uses threat intel dynamically for automated decision-making and response. | Matches IOCs during event correlation but relies on humans for action. |
| Analyst Workload | Significantly reduces workload by automating repetitive security tasks. | High manual involvement required for investigations and alert triage. |
| Best For | Organizations needing faster, consistent, automated threat response. | Organizations needing complete visibility, monitoring, and early detection. |
Although SOC uses SOAR and SIEM together to enhance security, their purpose, scope, and depth of operation are essentially different. A comparative description of the features of each technology in terms of its contribution to security is provided below.
1. Primary Role & Objective
SOAR is concerned with incident response and operational efficiency. It aims at making sure that all alerts are addressed rapidly and uniformly, even when security teams are overwhelmed. SOAR automates repeating processes and coordinates actions between endpoints, firewalls, identity systems, cloud applications, and ticketing solutions.
Comparing the primary role of SOAR vs SIEM, SIEM focuses on threat identification, log management, and security visibility. It gives you a single picture of all the activities occurring in the IT environment to easily detect suspicious patterns and new risks at the earliest.
2. Input & Data Sources
SOAR gets notifications of other cybersecurity software solutions, such as SIEM, EDR, XDR, email security, firewall, and cloud monitoring tools. It does not primarily collect raw logs; rather, it ingests enriched alerts and performs decision-making and automation.
SIEM receives raw logs and event data across the environment, like servers, endpoints, identity providers, networks, applications, databases, and cloud workloads. It is the focal point of event correlation and threat detection.
3. Alert Management & Prioritization
SOAR gives priority to alerts based on their severity, asset value, threat intelligence scores, and the playbook logic. It automatically filters noise to ensure that analysts are not overwhelmed with false positives.
SIEM uses alerts when anomalies are in line with set rules or behavioral patterns. However, prioritization is heavily dependent on tuning and manual review, which can slow down response if the alert volume is high.
4. Incident Response Ability
SOAR provides hands-on remediation using automated workflows. When an attack occurs, SOAR can instantly:
- Block IPs/domains
- Disable compromised accounts
- Force password resets
- Isolate endpoints
- Notify teams and create tickets
SOAR acts on incidents in minutes, sometimes within seconds, even without analyst intervention.
SIEM does not automatically remediate incidents. It notifies analysts of possible threats but requires manual investigation and action.
5. Automation & Playbooks
SOAR is built around automation playbooks. The incident response process can be standardized at every stage, including triage, containment, and documentation. Playbooks make it consistent and fast, even if a small group of people is working on it.
SIEM does not include automation playbooks for response. Although certain advanced SIEM tools offer some response capabilities, they do not offer orchestration but rather detection.
6. Threat Intelligence Utilization
SOAR proactively involves the use of threat intel in automated decision-making. For example, when an alert has an IP with a high malicious score, SOAR can block it automatically on security devices.
SIEM takes up threat intelligence to match indicators of compromise (IOCs) when correlating events, yet actions after the events still require human intervention.
7. Analyst Workload
SOAR is programmed to ease workloads. It is capable of doing repetitive work on its own, and analysts are only engaged in approvals or crucial decisions.
SIEM is analyst-dependent. Higher alert volume means more manual triage and investigation, creating potential burnout and delays.
SOAR vs SIEM – Real-World Use Cases
Below are real-world scenarios showing how each platform contributes differently to security operations:
1. Phishing Email Incident
SIEM identifies unusual login activities or email patterns by analyzing logs from Microsoft 365, Gmail, IAM, or endpoint logs.
SOAR reacts by quarantining the phishing emails in all mailboxes, blocking the sender domain, resetting credentials, warning the user, and updating the incident ticket.
2. Malware / Ransomware Infection
SIEM detects suspicious file execution, unauthorized encryption, or lateral movement patterns based on event correlation.
SOAR separates the affected endpoint from the network, initiates antivirus scans, blocks malicious processes, and updates the SOC dashboard automatically.
3. Privileged Account Misuse
SIEM identifies suspicious actions, e.g., accessing high-value data at an unusual time, accessing multiple locations, or multiple logs.
SOAR automatically disables credentials, requires multi-factor authentication, works on high-priority tickets, and notifies the HR or IT managers if necessary.
4. Cloud Security Threats
SIEM identifies misconfigurations on the cloud, unauthorized instance launches, or dangerous API calls on the basis of cloud activity logs.
SOAR reacts by blocking open resources, implementing security policies, and logging evidence of remediation.
5. Compliance & Audit Reporting
SIEM collects historical event data and generates detailed compliance dashboards (PCI-DSS, GDPR, ISO 27001, SOX, HIPAA, etc.)
SOAR organizes evidence, updates case records, attaches remediation logs, and closes tickets automatically.
SOAR and SIEM as a Unified Security System
While SOAR and SIEM each deliver significant value individually, their real power is unlocked when they work together. Most modern SOCs no longer choose between the two; instead, they integrate both to create an automated ‘detect → analyze → respond’ security loop.
Here’s what the unified workflow typically looks like:
1. SIEM collects logs and detects anomalies
- Pulls data from endpoints, networks, cloud, applications, IAM systems, and security tools
- Identifies suspicious patterns, behaviors, or policy violations
2. SIEM sends alerts to SOAR
- SIEM correlates events and flags incidents
- SOAR receives enriched alerts via API or native connector
3. SOAR determines the best response based on playbooks
- Uses severity, context, asset value, and threat intel to decide next steps
4. SOAR executes automated remediation
- Blocking malicious IPs/domains
- Disabling user accounts
- Isolating infected devices
- Closing malicious sessions
- Generating tickets and stakeholder notifications
5. SOAR updates SIEM and documentation
- Incident evidence and audit logs are updated
- Case status and metrics are automatically logged for reporting
Benefits of Using SOAR and SIEM Together
| Combined Impact | Result |
|---|---|
| Faster threat detection + automated response | Reduced time to contain attacks |
| Fewer false positives | Less alert fatigue for analysts |
| Consistent remediation | Standardized response across SOC shifts |
| Closed-loop visibility | Full traceability from detection to resolution |
| Lower operational cost | Teams handle more threats with less manual work |
SOAR and SIEM together transform a SOC from reactive to proactive, improving resilience against fast-moving cyberattacks without requiring a large team.
Best SIEM and SOAR Tools
Nowadays, cybersecurity teams rely on a mix of SIEM and SOAR tools, as it is equally important to detect threats early as to remediate them.
Splunk Enterprise Security is a popular choice among SIEM tools. It provides in-depth log analytics, effective dashboards, and robust correlation rules that enable security teams to identify suspicious activity at scale.

Splunk Enterprise Security
Starting Price
Price on Request
IBM QRadar is another SIEM tool that is unique because of its sophisticated analytics and the capability to swiftly map abnormal network patterns and threats. This speeds up the investigation.
The organizations that are looking for a cloud-native alternative can go for Microsoft Sentinel. It has gained popularity as a SIEM solution because it can easily be integrated into Microsoft-based environments. Also, it can ingest large amounts of hybrid and multi-cloud data without intensive configuration.

Microsoft Sentinel
Starting Price
Price on Request
On the SOAR side, Palo Alto Cortex XSOAR is regarded as one of the most robust orchestration platforms. It has hundreds of security tools connected to it and end-to-end workflows to automate incident response that can save the analyst hundreds of hours.

Cortex XSOAR
Starting Price
Price on Request
IBM QRadar also comes as a reputable SOAR solution that is widely used. It enables teams to manage incidents by using playbooks that are well organized and tend to modify themselves automatically according to the threat conditions.
Splunk SOAR would also be a good option for security specialists who require a more abstracted use of its wide collection of integrations and drag-and-drop playbook builder, which makes automation accessible even for analysts without coding experience.
Many organizations adopt SIEM and SOAR tools together rather than choosing one over the other. For example, Sentinel or Splunk can collect and correlate logs to detect threats, while Cortex XSOAR or IBM Resilient can automatically trigger containment actions like isolating endpoints or blocking IPs.

Splunk SOAR
Starting Price
Price on Request
Conclusion
SOAR and SIEM are not rivals, but complementary components of the current cybersecurity system. SIEM provides the security teams with the insight they require by gathering logs, identifying threats, and warning signs within the IT environment. SOAR goes one step further by coordinating with other security tools, automating the response, and ensuring threat mitigation takes just minutes.
Although both platforms offer individual value, they are even stronger when united as a single mechanism.
Mehlika Bathla is a passionate content writer who turns complex tech ideas into simple words. For over 4 years in the tech industry, she has crafted helpful content like technical documentation, user guides, UX content, website content, social media copies, and SEO-driven blogs. She is highly skilled in... Read more