The same passwords that protect us every day can quickly become a liability if they are not stored or managed securely. One of the most dangerous threats in this area is the rainbow table attack.
It is faster than brute-forcing, more deceptive than dictionary attacks, and highly effective against systems still relying on outdated password protection methods.
Even though the rainbow table attacks are not new, they still persist. Passwords are still stored in many organizations using weak hash functions, and people are still using weak and predictable passwords. Without appropriate defense mechanisms, a hacker can crack hashed passwords within minutes with ease.
This guide breaks down everything you need to know
- What rainbow table attacks are
- How they work
- How they can impact organizations of all sizes
- And most importantly, how to prevent them using practical and modern techniques
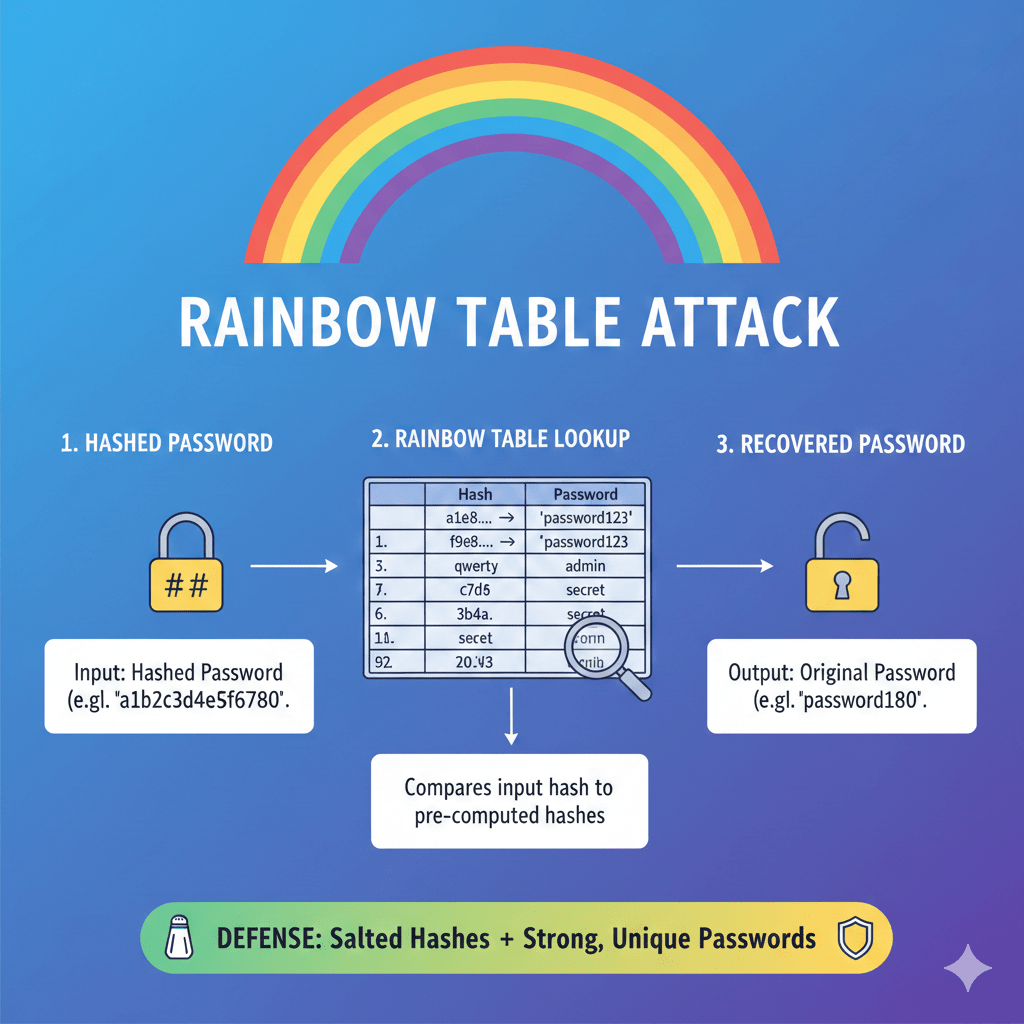
What Exactly Is a Rainbow Table Attack in Cybersecurity?
Your password is never stored in unencrypted form on your computer or application. Rather, it alters the password to a garbled string of characters via a mathematical algorithm. This is referred to as hashing, and the outcome is a hash!
A hash represents a cryptographic signature of your password.
One of the main characteristics of hashing is that it is unidirectional. You can hash a password, but you cannot mathematically undo a hash to obtain the original password.
This is where the rainbow table attacks prove to be dangerous. The hash functions are predictable. When you hash the same password using the same algorithm many times, you will get the same output each and every time.
Cybercriminals take advantage of this predictability and construct massive databases known as rainbow tables, which store millions of common passwords and their hash equivalents. After stealing hashed passwords in a system, all that they have to do is to search the hashes in their table. When there is a match, they automatically have the original password.
Concisely, rather than spending time cracking passwords individually, a rainbow table enables attackers to bypass the guessing game; hence, the technique is remarkably quick.
A Simple Rainbow Table Attack Example to Understand
Imagine a hacker gets hold of a database that contains a value like:
482c811da5d5b4bc6d497ffa98491e38
A user might assume they are safe because the real password isn’t visible. But if the hacker has that hash stored next to password123 in their rainbow table, your account is instantly compromised.
What makes the situation worse is that many users reuse passwords across platforms. Once attackers discover just one password, they can attempt to break into bank accounts, emails, shopping sites, and more. It’s like a ripple effect that can spiral quickly.
How Do Rainbow Table Attacks Work?
To be on defense, it is useful to know how the attack works:
The attacker obtains hashed passwords first, usually through some vulnerabilities such as SQL injection, weak server security, weak data transmission, or insider attacks.
They match the stolen hash values with their rainbow table. In case of a match, the respective password is displayed.
In case there is no direct match, the attacker uses a reduction function and repeats the lookup process until the hash finally results in a matching plaintext password.
When the attacker has the password, they can access the system without leaving much trail, since the unsuccessful logins are not shown as alerts.
Why Rainbow Table Attacks Are Still Used Today?
Rainbow tables may appear outdated given the current developments in cybersecurity. Nevertheless, they are still applicable since:
- Most old systems still rely on the outdated hash functions, including MD5, SHA-1, LM Hash, and NTLM, all of which are very easy to map in rainbow tables.
- A large number of organizations are using old passwords or poorly secured backups.
- And complex rainbow tables demand a high initial cost with a payoff of years of reuse.
Rainbow tables are especially popular with attackers since after they have stolen the database, they do not need to deal with the live system. This makes the intrusion very hard to detect.
What Can Happen After a Rainbow Table Attack?
A rainbow table attack opens the gate to diverse business risks:
- Hackers have access to inside networks with the use of stolen employee accounts.
- They are able to view customer confidential data and financial records. Stolen credentials can be used in multiple services to impersonate other accounts.
- Attackers are able to increase privileges and install ransomware or malware.
- Some of the fallouts can be loss of revenue, lawsuits, regulatory fines, and reputational loss in the long term.
The 2012 LinkedIn attack is one of the most famous warnings. Millions of hashed passwords were stolen, and they were unsalted and weakly secure. The passwords were reused later on the internet, and account takeovers swept the internet.
That was over ten years ago, but even now, numerous companies do not implement modern hashing security, and that is why the rainbow table attacks are still persisting.
Brute Force, Dictionary and Rainbow Tables
In a brute force attack, all combinations are attempted to find a password. In dictionary attacks, real words and frequently used passwords are employed in a list. They both tend to create numerous unsuccessful login attempts, which can be detected by cybersecurity tools.
Rainbow table attacks do not involve any guessing; once the hashed passwords have been stolen, the cracking is fully offline. It implies no failed attempts to log in, no warning, and no rate-limiting to prevent the hacker. They are able to work silently and freely up to the time when all the passwords are decoded.

SentinelOne
Starting Price
Price on Request
How to Protect Against Rainbow Table Attacks?
The positive thing is that rainbow table attacks can be prevented considerably. It only demands that companies and developers modernize the password storage and authentication methods.
1. Always Salt Passwords Before Hashing
The best defense against rainbow tables is salting. Before hashing, a unique random string is added to the password, which is known as a salt. It implies that two users sharing a password will be assigned entirely different hash values, and prebuilt rainbow tables will be useless.
Assuming a rainbow table held the hash of password123, but the real stored value was password123A8k%2R7, and it is hashed, the attacker cannot align it with anything in the table.
This is why salts must be:
- Generated randomly
- Unique for every password
- Stored securely alongside the hash
When passwords are salted, attackers cannot build universal rainbow tables, and any theft of hashed passwords becomes much harder to exploit.
2. Use Strong, Modern Hashing Algorithms
Legacy algorithms like MD5, SHA-1, and LM Hash are too fast and predictable. Modern hashing algorithms like bcrypt, scrypt, PBKDF2, and Argon2 are intentionally slow, forcing the system to take longer when hashing. That delay, although small for users, dramatically increases the time required for attackers to crack passwords.
Consider it like increasing the thickness of a safe wall, even if someone has tools to break in, it takes far longer and discourages attacks.

Singularity Cloud
Starting Price
Price on Request
3. Regularly Update Hashing and Authentication Systems
Password storage security is not a ‘set-and-forget’ concept. Standards evolve, and attackers get smarter. Organizations should:
- Periodically review which algorithms are being used
- Migrate away from outdated hashing functions
- Rehash stored passwords after upgrades during user login or password reset
Many cyber breaches occur simply because companies continue using practices that were considered secure ten years ago.
4. Strengthen Password Quality
Technical defenses are strong; however, human behaviour is the weakest. Attackers construct rainbow tables with the most predictable passwords, and, unfortunately, millions of users use such passwords as 123456, password, or their date of birth. Random passwords, which contain long and random characters, stand little chance of appearing in rainbow tables.
So, you can create strong passwords easily by using password managers, even if you are a non-technical user.
5. Turn On Multi-Factor Authentication (MFA)
MFA adds an additional verification step beyond the password, such as a one-time code, a mobile prompt, biometrics, or a physical security key. Even if a rainbow table reveals a password, the attacker cannot access the account without the second factor.
MFA doesn’t replace strong password storage, but it provides a safety net that prevents stolen passwords from being immediately useful.

ThreatCop
Starting Price
Price on Request
6. Focus on Broader Server and Network Security
The first phase in a rainbow table attack is password theft, and therefore, it is important to minimize the attack surface. Patch management, encrypted transmissions, network segmentation, and limited privilege access ensure that hackers find it much harder to steal hash databases.
Cybersecurity is most effective when each layer supports the others.
Real-World and Hypothetical Scenarios
A small hospital has been using a patient portal that was built ten years ago. Unsalted SHA-1 is used to store passwords. In the case of an unpatched vulnerability, hackers steal thousands of hashes and decrypt them with rainbow tables to reveal patient records and medical billing information.
A global retailer hashes with a powerful hash algorithm; however, old login backups, stored on a third-party server, continue to be hashed with MD5. After those backups are leaked, attackers use the cracked passwords to gain VPN access to the company’s internal environment.
A government employee reuses the same password for multiple internal systems. While the agency’s primary system uses secure hashing, an older internal portal does not. After a rainbow table attack on the outdated system, attackers reuse the stolen password to log into more sensitive applications.
In each case, the outcome could have been prevented with salting, modern hashing, and better authentication hygiene.

Sophos SafeGuard Encryption
Starting Price
Price on Request
Final Takeaway
Rainbow table attacks are effective because too many systems still rely on outdated password storage practices. The solution is not complex:
- Salt every password
- Use modern hashing functions
- Avoid outdated algorithms
- Enforce strong passwords
- Enable MFA wherever possible
With the right defenses in place, rainbow table attacks become not just difficult but practically useless.
Mehlika Bathla is a passionate content writer who turns complex tech ideas into simple words. For over 4 years in the tech industry, she has crafted helpful content like technical documentation, user guides, UX content, website content, social media copies, and SEO-driven blogs. She is highly skilled in... Read more





























