Quishing Attack Explained: The QR Code Scam You Must Avoid!

From restaurant menus to parking meters; from delivery labels to payment counters; from conference check-ins to office doors, QR codes are everywhere today. Their widespread take-up is, in part, due to their seemingly harmless outlook and ease-of-use. All you need to do is to point your phone at them, scan, and tap.
This simple habit is exactly what cybercriminals are turning into a new kind of phishing trap, commonly called the quishing attack. If your team, your customers, or even your family use QR codes regularly, quishing should be on your radar.
Let’s learn about it in detail, so you know what it is and how to stay safe, one cybersecurity solution at a time.
What is a Quishing Attack?
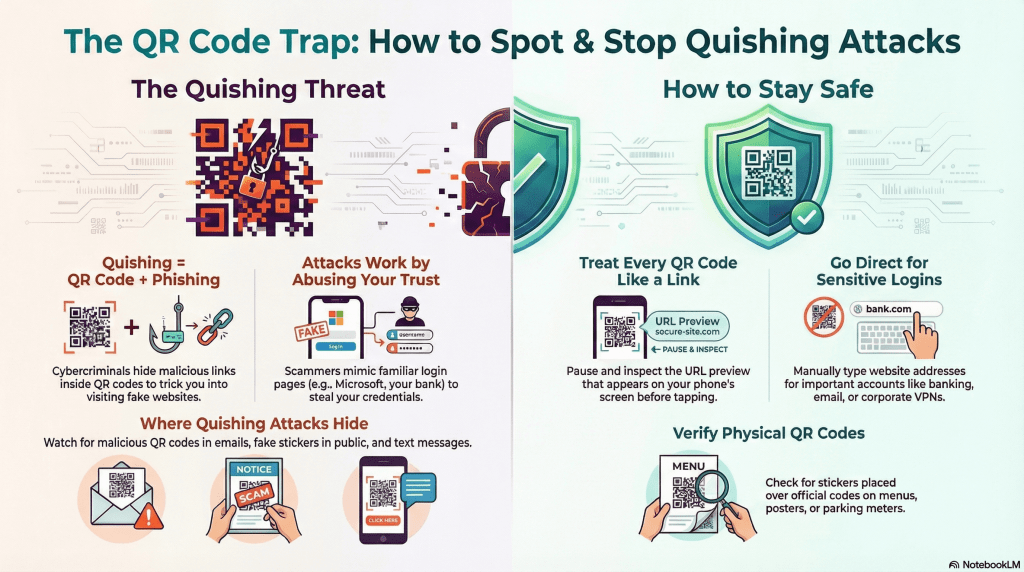
A quishing attack is a type of phishing scam that makes use of QR codes instead of clickable links in emails or text messages to trick people. The term quishing itself is an amalgam of ‘QR’ and ‘phishing’.
Rather than sending a suspicious link that users might recognize and avoid, attackers embed the malicious link within a QR code. When the victim scans the code, their device opens a fraudulent website that is designed to steal sensitive information such as login credentials, payment details, or even install malware.
In some cases, it can trigger unauthorized actions like sending messages or approving transactions. This QR code scam is the same old phishing tactic, but this time disguised as a black-and-white square.
The danger lies in the fact that people often choose to ignore or verify URLs on desktops, but this habit often disappears when dealing with QR codes, making them a weapon for cybercriminals.
Suggested Read: What is Smishing?
How Does a Quishing Attack Work?
Most quishing attacks follow a familiar pattern, just with a QR code in the middle.
Step 1: Get your attention
A quishing attack starts with something that looks completely normal. It could be a work email from IT support, a delivery note on your door, or even a printed sign near a payment kiosk.
Somewhere on it, there’s a QR code and a message that sounds normal, like ‘Scan to verify your account’, ‘Scan to appeal this fine’, or ‘Scan to access Wi-Fi’. These messages are designed to make you act quickly without thinking.
Step 2: You use your phone camera
Because QR codes feel official, you trust them. You open your phone camera and scan the code. Instantly, your phone opens a browser page, and you assume everything is fine.
Step 3: Fake site
The page you land on looks just like something you know, maybe Microsoft 365, Google, your bank, a payment portal, or your company’s VPN login page. This familiar design is intentional. It lowers your guard and makes you believe the site is real.
Step 4: You enter details
Next, you enter your details, such as your username, password, card number, or OTP. The attacker collects this information immediately. In some cases, the fake site even redirects you to the real one afterward, so you don’t suspect anything unusual.
Step 5: Attackers use your access
Once they have your details, attackers can log into your accounts, reset passwords, move money, send more QR scams using your identity, or even break into company systems. From your point of view, you only scanned a QR code and logged in as usual. From their point of view, that little square just did all the work.
Suggested Read: What is Vishing and Why It Matters?
How are QR Code Scams Carried Out?
Attackers use both digital and physical channels to launch a quishing attack. This mix makes them hard to spot and easier to trust.
1. Email-based Quishing
One of the most common methods is through email. You might receive a message warning about a blocked account, expired password, or missed payment. Instead of a clickable link, the email contains an image of a QR code with instructions like ‘Scan this QR code with your phone to secure your account’.
Attackers use images because email security tools often scan links, and hiding the phishing link inside a QR code can bypass those filters more easily than a plain text URL.
2. Printed QR Code Scams
This approach is even sneakier. Attackers place fake QR code stickers over real ones in public places such as parking meters, restaurant tables, EV charging stations, or event posters.
You think you are paying for parking or checking a menu, but instead, you land on a phishing page or a fake payment site. These scams work because they appear in places you already trust, and scanning QR codes in these settings feels normal, so you rarely question the source.
3. Smishing (SMS) With QR Codes
Some scams arrive via text messages. You might see messages like ‘Your package is waiting. Scan this QR code to complete delivery’ or ‘Your bank account is locked. Scan to restore access’. When you scan the code, you are taken to a fake login or payment page designed to steal your details.
4. Workplace & Business Scams
Employees are frequent targets because attackers know they are under time pressure and may scan quickly. Common examples include fake IT support notices asking staff to scan a QR code to reset VPN credentials, fake HR or payroll messages requesting scans to view tax forms, and even fake meeting invites with QR codes for ‘secure access’.
Common Targets of Quishing Attacks
While anyone can fall for QR scams, some groups are targeted more often. Employees and corporate accounts, for instance, are their prime targets because attacking them gives them access to confidential files, emails, and internal tools. They also get to reuse passwords and impersonate staff, especially remote workers who rely on QR codes for Wi-Fi and event check-ins.
Small and mid-sized businesses are also vulnerable since they often lack full-time security teams yet handle sensitive data, making finance staff, owners, and front-desk employees easy marks for fake invoices or bank notices.
Consumers paying via QR codes face risks from fraudulent charity posters, tip jars, and ‘scan-to-pay’ signs at restaurants or parking lots, particularly when rushed or distracted.
Students and younger users scanning codes for classes or campus events, too, are easily tricked by fake scholarship emails or job flyers, often skipping checks on where the QR leads.
Suggested Read: Phishing vs Vishing vs Smishing – Detailed Comparison
How to Know If You are Becoming a Victim of Quishing?
Not every QR code is dangerous, but it is important to recognize when something feels off. One major warning sign is pressure and urgency, messages that push you to act fast, like ‘Scan now or your account will be closed’ or ‘Immediate action required’, are designed to stop you from thinking.
Another red flag is requests for sensitive data. If scanning a QR code takes you to a login page or asks for your bank details, Social Security number, or payment approval, it is likely a scam.
Always check the website URL after scanning. Look for odd spellings, random domains, or unusual country codes that don’t match the business name. Physical QR codes can also be suspicious if they look out of place, such as crooked stickers, peeling labels, or codes covering official signs.
Finally, consider the source. If the QR code comes from an unexpected email, text, or unknown sender, or asks you to do something unusual, treat it as suspicious.
Preventive Measures Against Quishing
You don’t need to be a security expert to stay ahead of quishing attacks. A few habits go a long way…
1. Treat QR Codes Like Links
Every QR code is just a link in disguise. Before you open it, check the URL that appears on your phone’s screen when you scan. Both iPhone and Android show the link at the top or bottom. Pause and read it carefully.
If the address looks strange or doesn’t match the business name, don’t tap. Make this a habit, especially for QR codes related to payments, banking, or logins.
2. Type Sensitive Sites Manually
For important sites like online banking, corporate email or VPN, payroll portals, or government websites, avoid scanning QR codes from emails, flyers, or text messages. Instead, type the web address directly into your browser. This simple step helps you bypass fake links hidden behind QR codes.
3. Verify Physical QR Codes
When scanning printed or posted QR codes, take a moment to check if a sticker has been placed over another code. If you are unsure, ask staff whether the payment or menu QR code is official. If in doubt, request a manual payment option or a printed menu. Many businesses are aware of QR-based fraud and will understand if you ask.
4. Use Security Tools on Your Phone
While no tool catches everything, enabling safe browsing features on your phone can help. You can also make use of a mobile security software solution that checks URLs against known malicious sites.
Don’t forget to keep your phone’s operating system and browser updated so threats are blocked faster. These steps, when combined together, can prevent some QR scams before they fully load.
5. Train Employees & Set Clear Rules
For businesses, protecting against quishing attacks requires both technology and awareness. Conducting short training sessions to explain QR phishing risks can help. You can also set internal rules stating that IT, HR, or finance will never ask for passwords or MFA codes via QR scans.
Companies can also provide clear guidance on how to verify any email or flyer with a QR code. Basically, encouraging a culture where employees feel safe asking, ‘This QR looks odd, can someone check?’
6. Lock Down Official QR Usage
If your company makes use of QR codes for marketing, events, product packaging, or guest Wi-Fi, take precautions. Only use domains you control and keep them consistent. Also, educate customers and staff about what official QR codes look like and where they appear.
7. Encourage Reporting & Quick action
If someone comes across a suspicious QR code or falls for one, ask them to immediately report it to the IT or security teams. Reset passwords and check for unusual account activity. If, God forbid, money was involved, contact the bank or card issuer quickly to raise dispute for unauthorized transactions. Remember only fast reporting can limit damage and help others from falling into the same trap.
Conclusion
Quishing attacks, all in all, convert our trust in QR codes into a weapon. The risk thus is real, but so is the road to prevention. All you need to do is to pause and think before you scan any QR code and even if you do, don’t forget to question it if request logins, payments, or personal data is what it asks for.
By treating fake QR codes with the same caution as links, you can keep most QR phishing attempts at bay way before they start. Taking help from a good cybersecurity solution is another way for you to steer clear of them.
Just give us, at Techjockey, a call and get the best security solution working for you today itself!
Yashika Aneja is a Senior Content Writer at Techjockey, with over 5 years of experience in content creation and management. From writing about normal everyday affairs to profound fact-based stories on wide-ranging themes, including environment, technology, education, politics, social media, travel, lifestyle so on and so forth, she... Read more




























