Latest Posts
When to Deploy Wireless Intrusion Detection System (WIDS): 7 Signs Your Business is in Danger
 By Jasmeet Kaur February 19, 2026
By Jasmeet Kaur February 19, 2026
In a modern enterprise, Wi-Fi is like air. It is invisible, essential, and everywhere. But because it’s invisible, it’s also one of the hardest assets to...
Top 5 Private Instagram Viewer: Features & Risks Explained











Users often search the Internet to find a private Instagram viewer tool when they want to find out what is going on in a restricted account....
Top 6 Asset Performance Management Solutions in 2026











Unplanned downtime costs industrial businesses nearly $50 billion every year, with equipment failure responsible for a major share. For asset-heavy industries, even a few hours of...
The Hidden Cost of Payment Gateways: Margin Leakages You Don’t See and How Airpay Fixes Them











Speed and user convenience are mostly the standard elements weighed when choosing a payment gateway. Businesses often favor a fast installation, smooth checkout flow, and clear...
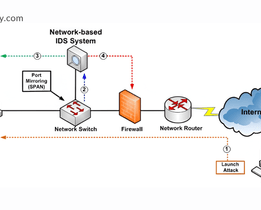
What Is a Network Intrusion Detection System? Types, Tools & NIDS vs HIDS











In today’s digital era, networks power everything from emails and payments to business operations. Traditional security tools are inadequate because cyberattacks are becoming more intelligent and...
6 Best Anti Spyware Software in 2026











Spyware can quietly be the most dangerous form of malware. It tracks your activity, takes away sensitive data, and monitors your system when you are not...
Valentines Day Couple AI Prompts: Create Magical Romantic Photos











Valentine’s Day is all about love, memories, and beautiful moments. But what if you could create dreamy romantic pictures without booking a photoshoot? With tools like...
6 Best Employee Advocacy Platforms to Boost Engagement in 2026











You cannot consider your employees just as staff members; they are powerful brand ambassadors of your organization. An employee advocacy platform, when used in organizations, can...
Why Merchants Need Smart Routing and How Touras Can Assist?











Digital payments are the main pillar of contemporary merchanting activities in every market and user group. That said, shoppers today look for transactions that are immediate,...
What Is Pretexting? A Hidden Social Engineering Tactic Explained











Pretexting is one such term in the field of cybersecurity that is quite abstract until you notice how common the situation is in reality. In its...